Hack the box academy - Attacking web applications with Ffuf write up
INTRODUCTION
This walkthrough explains an in-depth use of Ffuz a web brute forcing tool based on hackthebox academy module that can help penetration testers identify hidden files or directions in the website. This massive tool helps unearth the following:
- Fuzz for directories
- Fuzz for files and extensions
- Identifying hidden vhosts
- Fuzz for PHP parameters
- Fuzz for parameter values
Introduction to Ffuf
Ffuf comes pre-installed in kali linux, or if it is not installed, you can easily install it using the following command sudo apt install Ffuf. For a better understanding of the tool’s usage, just type man ffuz or ffuz –help.
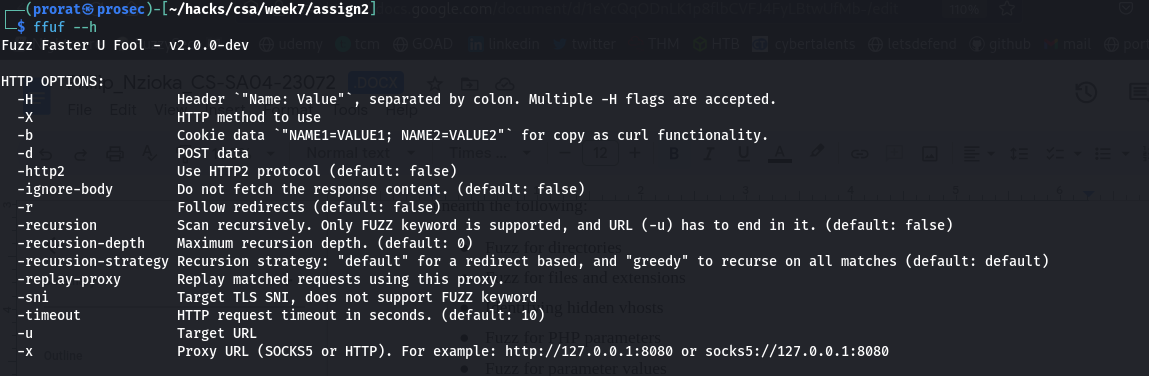
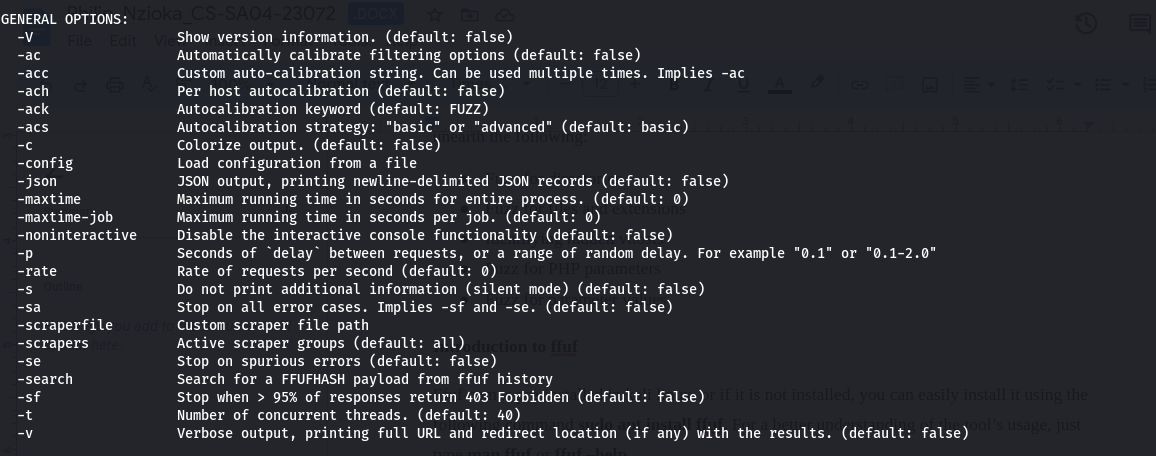
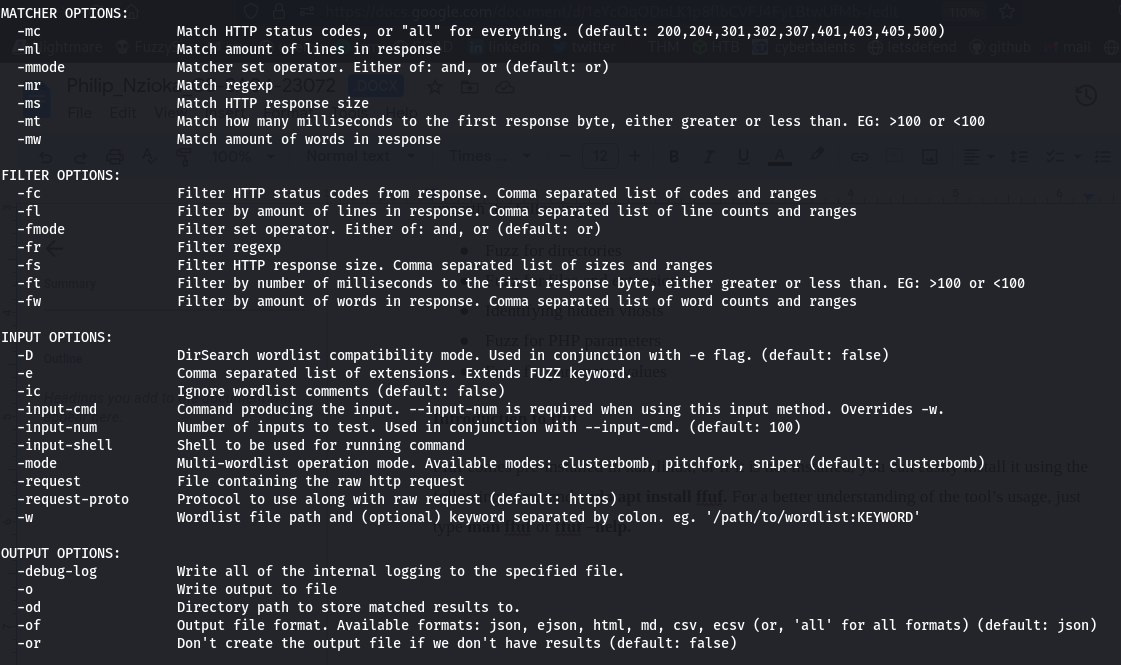
The help menu or the manual page provides so much information that can help the pentester utilize the tool to its best and get a well filtered output. We first the the https options section of the help menu, this where we get the flags to use that deal with the protocols, cookies, proxies and the nature of the request.
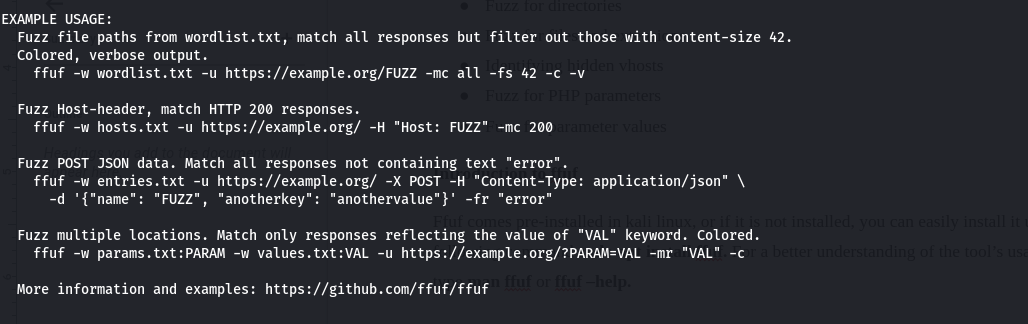
This section of the help menu shows the example of the commands and how to use the flags from the above sections.
Basic fuzzing using Ffuz
Fuzzing refers to a testing technique that sends various types of user input to a certain interface to study how it would react. usually utilize pre-defined wordlists of commonly used terms for each type of test for web fuzzing to see if the web server would accept them. One of the most commonly used wordlists is seclists,,which categorizes wordlists under various types of fuzzing, even including commonly used passwords. It can be installed directly to the kali machine by running the command sudo apt install seclists or cloning it from the github repository.
or by default, in the /usr/share/wordlists directory there are different wordlists and symlinks to wordlists that you may use.
Lab
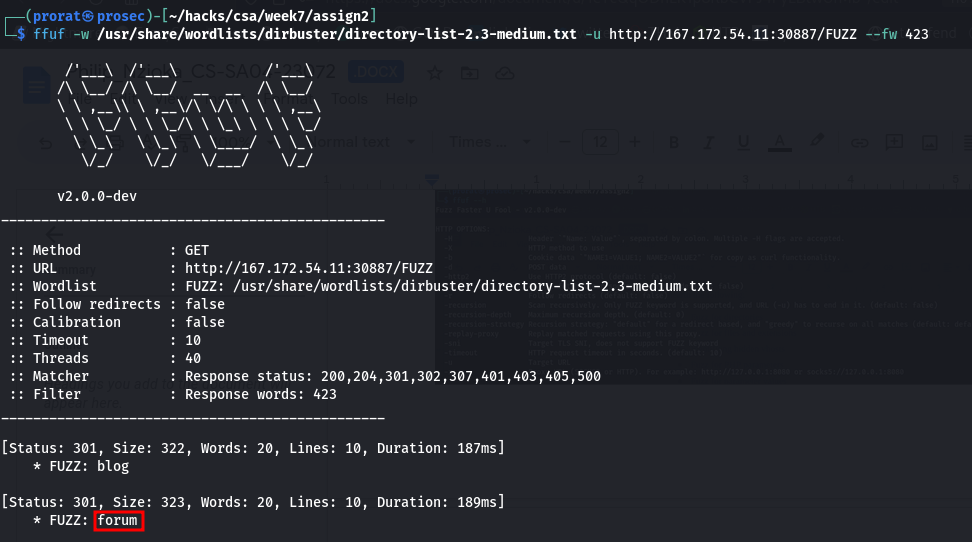
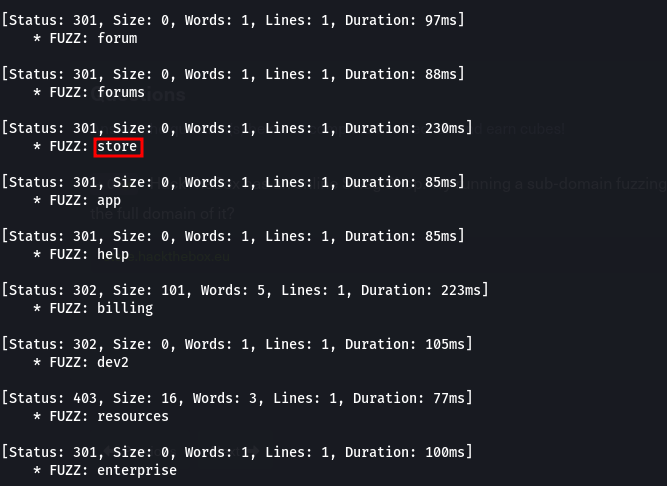
In the first lab question we are asked to find other directory:
q1. In addition to the directory we found above, there is another directory that can be found. What is it?.
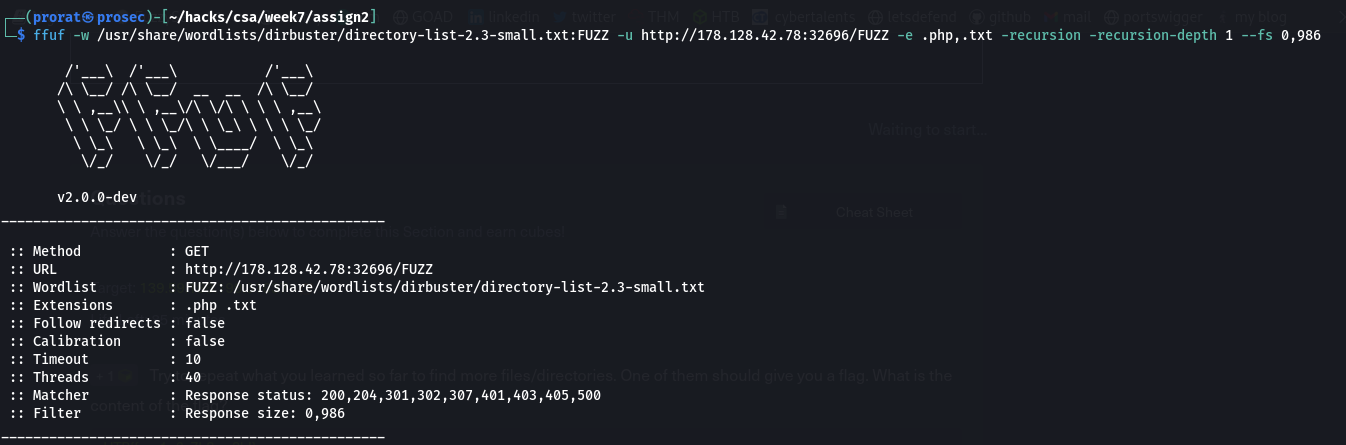
For this question we do a simple scan against the target. In the ffuz command, we just use the flag -w to specify the path to the wordlist that we are going to use. then -u for the target url and finally –fw to filter the meaningless output by words.
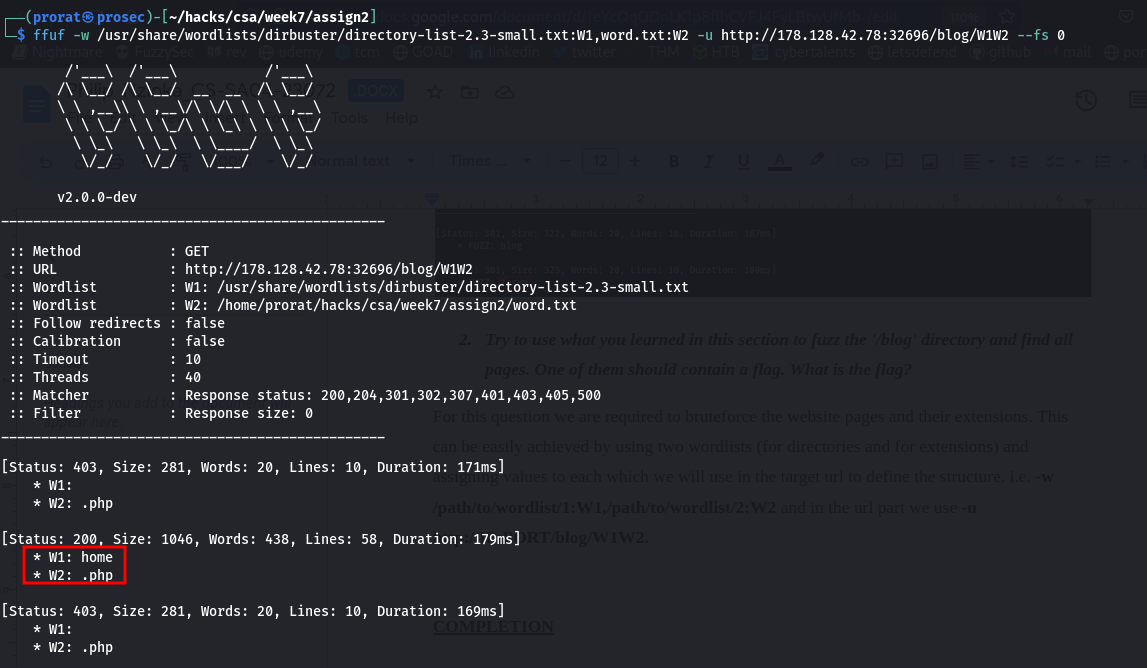
q2. Try to use what you learned in this section to fuzz the '/blog' directory and find all pages. One of them should contain a flag. What is the flag?
For this question we are required to bruteforce the website pages and their extensions. This can be easily achieved by using two wordlists (for directories and for extensions) and assigning values to each which we will use in the target url to define the structure. i.e. -w /path/to/wordlist/1:W1,/path/to/wordlist/2:W2 and in the url part we use -u http://IP:PORT/blog/W1W2.
Visiting the page home.php, we get the flag.
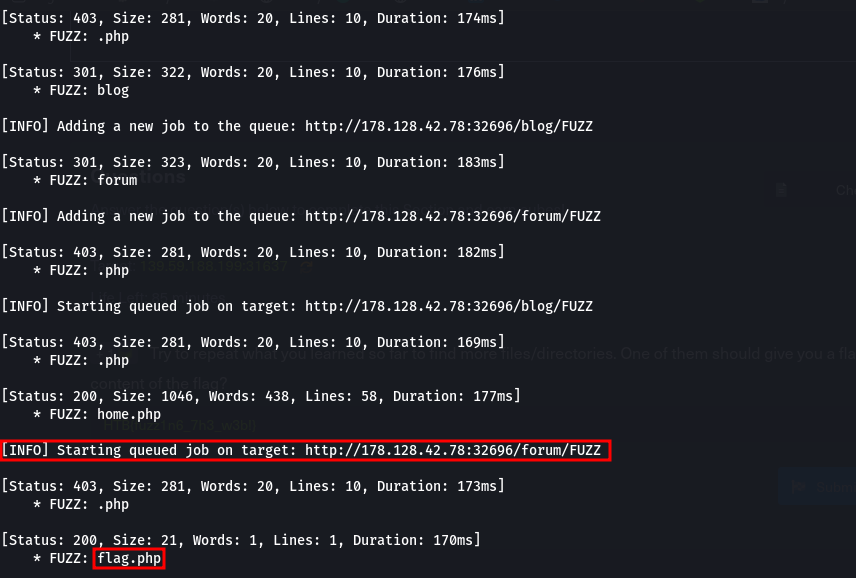
q3. Try to repeat what you learned so far to find more files/directories. One of them should give you a flag. What is the content of the flag?
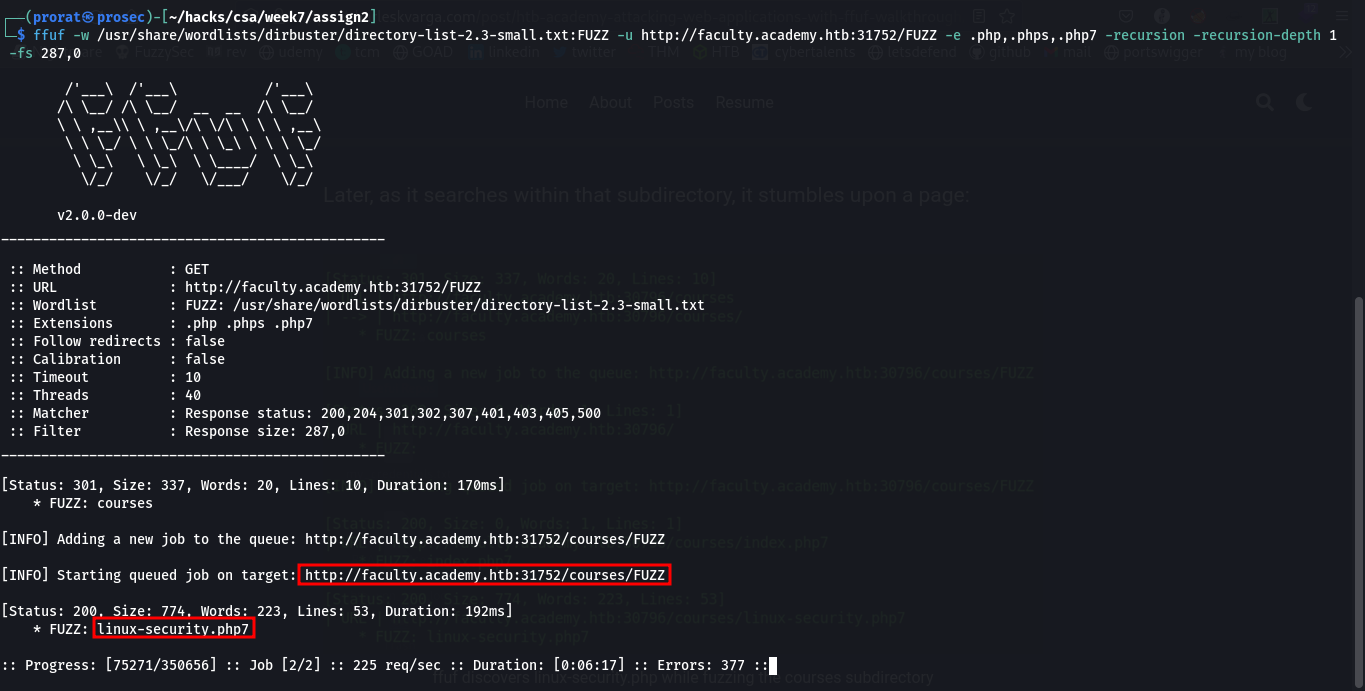
Here, we were required to perform a Ffuz scan on the website recursively. This means that it will automatically start another scan under any newly identified directories that may have on their pages until it has fuzzed the main website and all of its subdirectories.
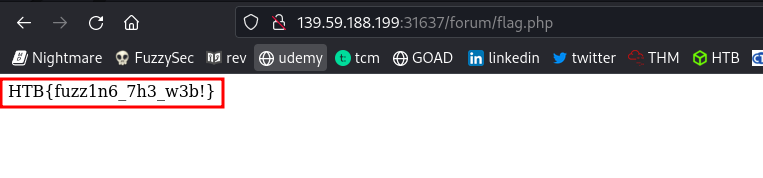
we’ve found that our flag.php file is in the forum directory. Visiting it in the browser we get the flag.
Sub-domain fuzzing
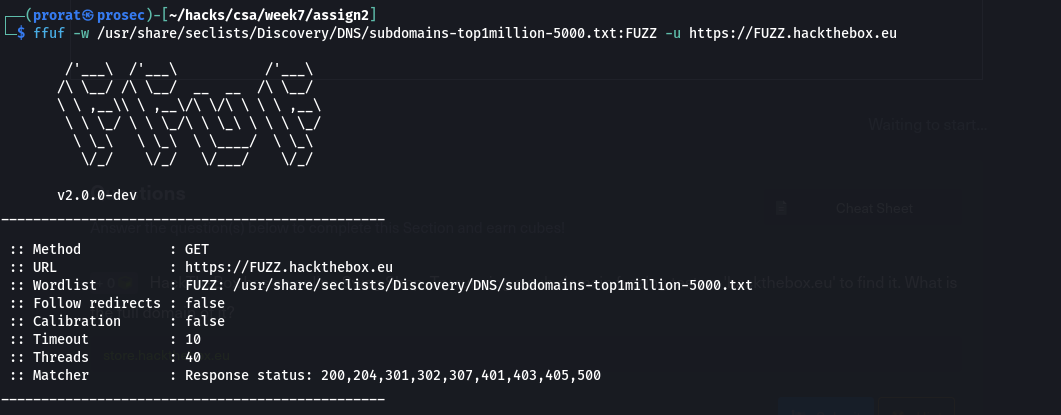
A sub-domain is any website underlying another domain. To brute force them using ffuz, we just place the value, in this case before the domain, For example; FUZZ.hackthebox.ke.
Question: HackTheBox has an online Swag Shop. Try running a sub-domain fuzzing test on 'hackthebox.eu' to find it. What is the full domain of it?
Vhosts Fuzzing
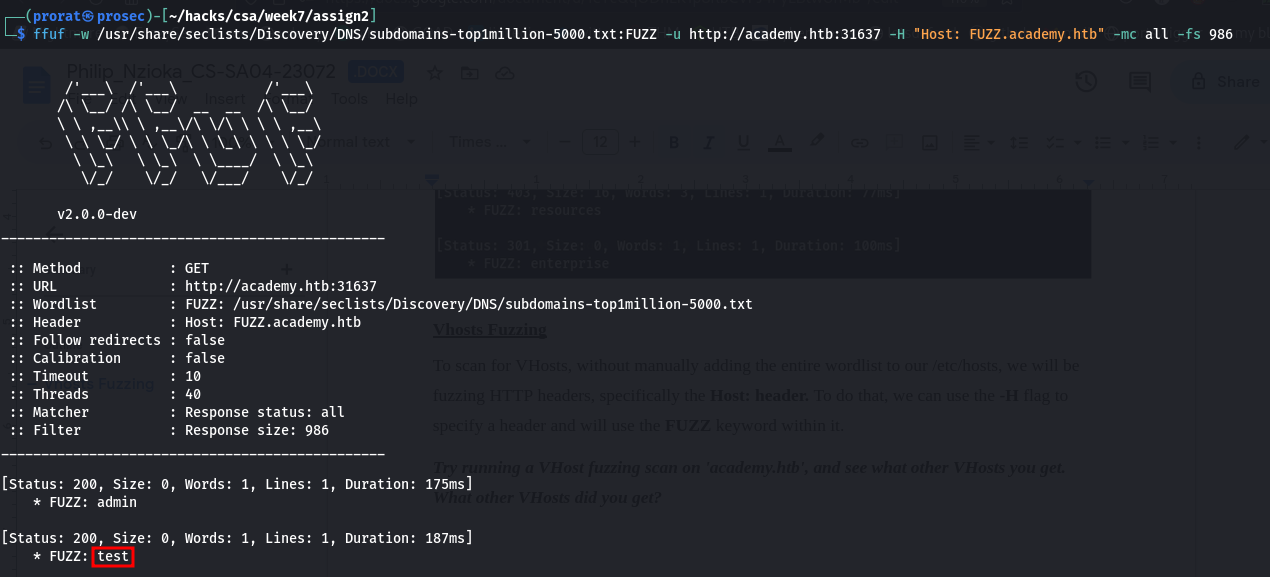
To scan for VHosts, without manually adding the entire wordlist to our /etc/hosts, we will be fuzzing HTTP headers, specifically the "Host: header". To do that, we can use the -H flag to specify a header and will use the FUZZ keyword within it.
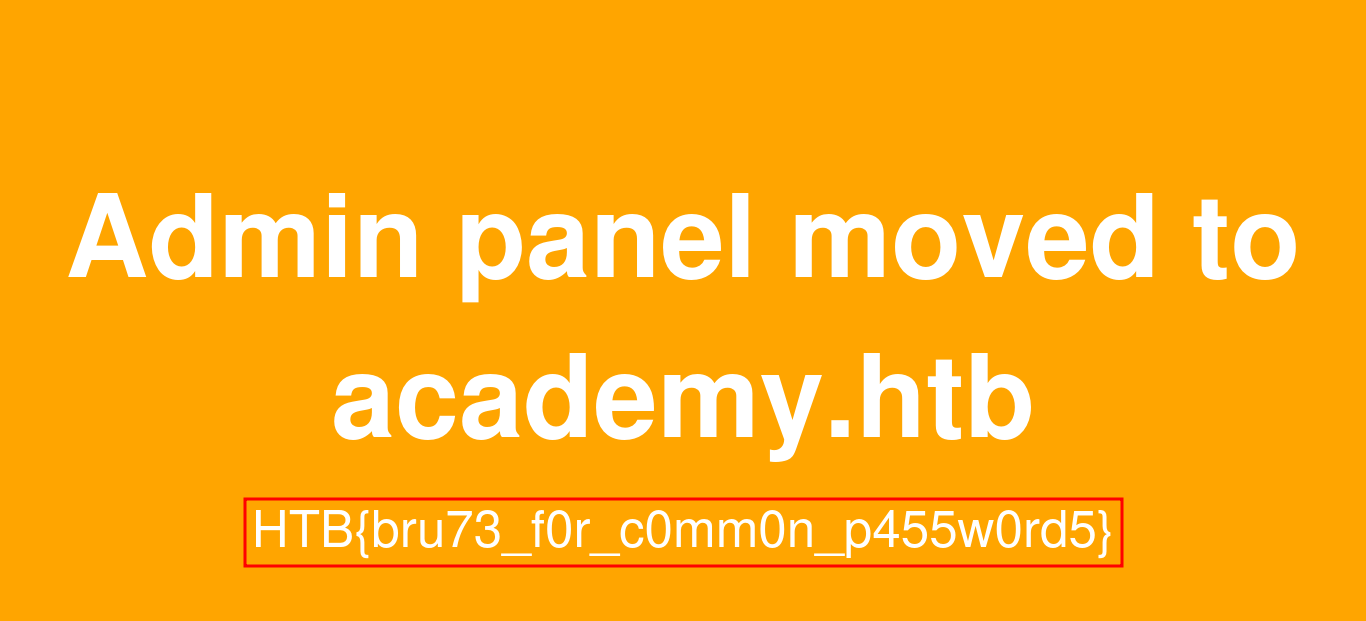
Question: Try running a VHost fuzzing scan on 'academy.htb', and see what other VHosts you get. What other VHosts did you get?
Parameter fuzzing
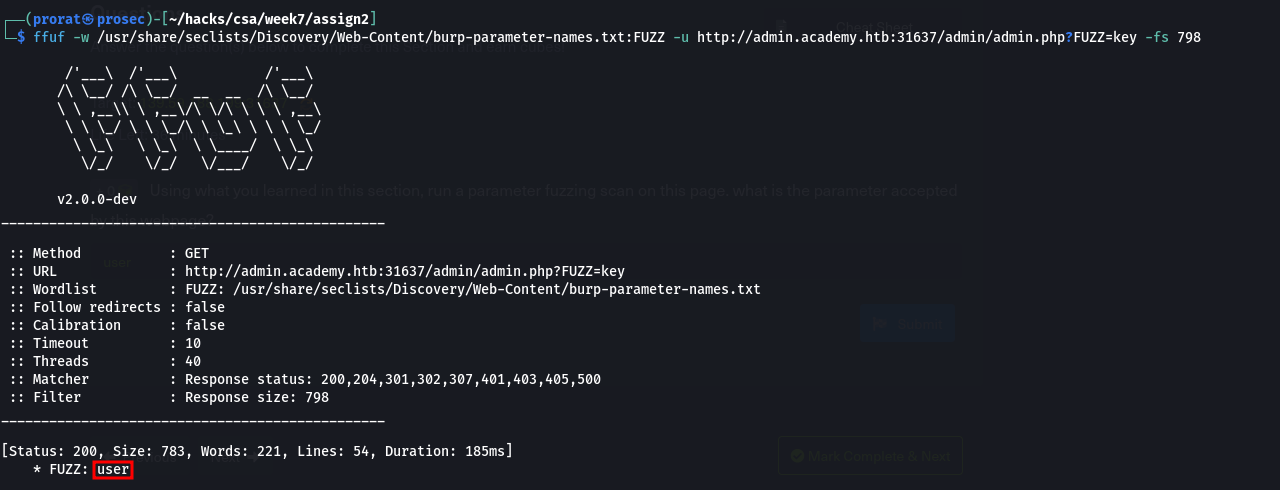
GET request
So, for example, trying to brute force the parameter for httx://admin.academy.htb:PORT/admin/admin.php param1=key all we have to do is replace param1 in the example above with FUZZ and rerun our scan with an appropriate wordlist in place.
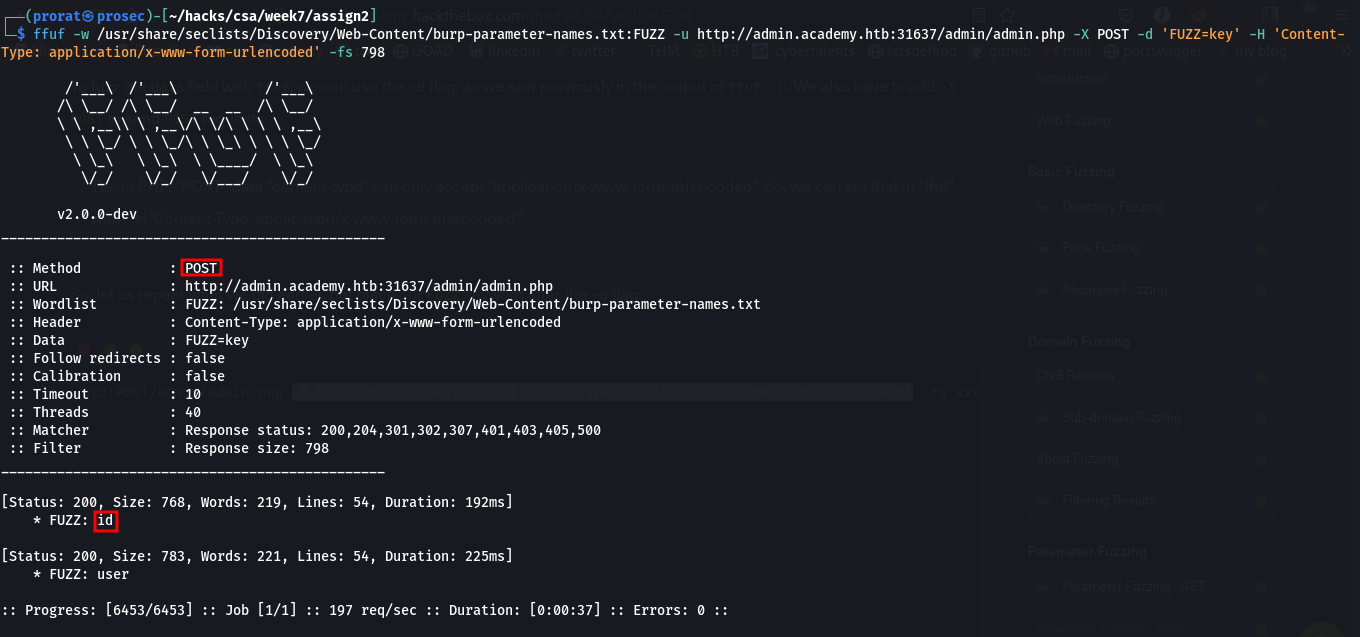
POST request
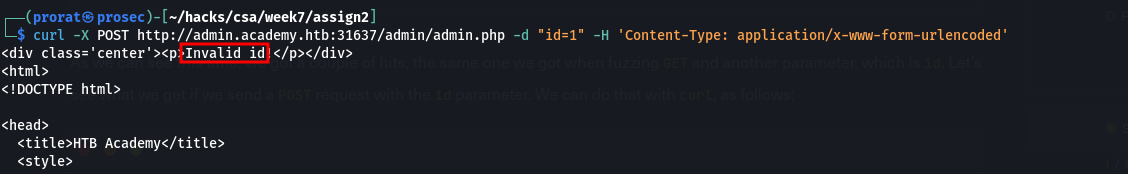
POST requests are passed in the data field within the HTTP request. To fuzz the data field with Ffuz, we can use the -d flag and add -X POST to send POST requests. we get another parameter id.
Trying to access the page with the id parameter and a random value, we get an invalid id error.
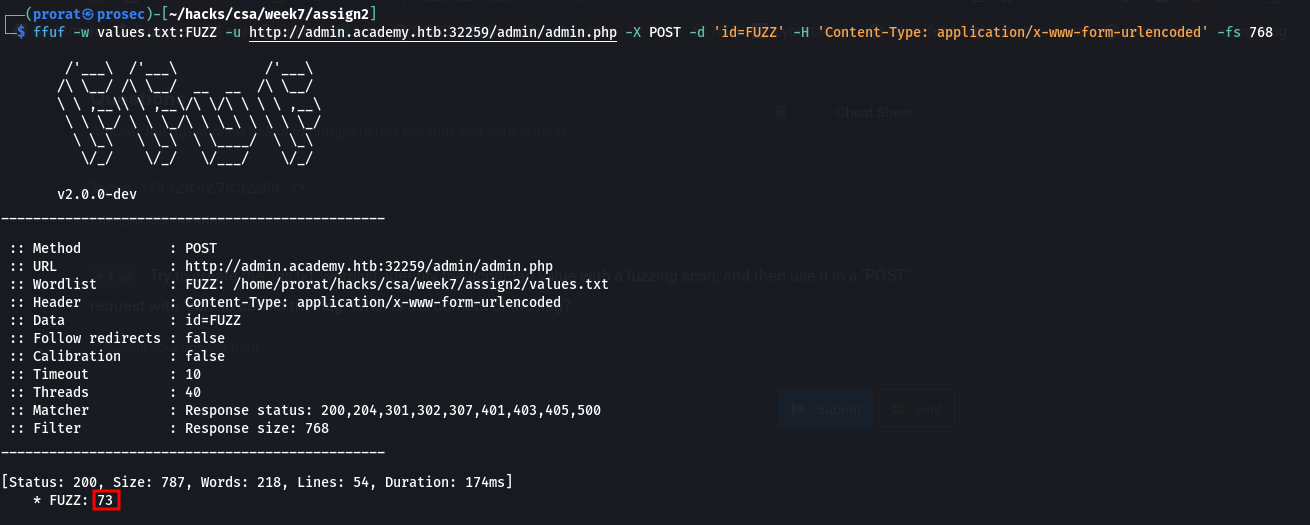
we create a list of parameters using python in our terminal and try to brute force it using the POST method and the id parameter we just found.
1
python3 -c 'for x in range(1,1000): print(x) > values.txt'
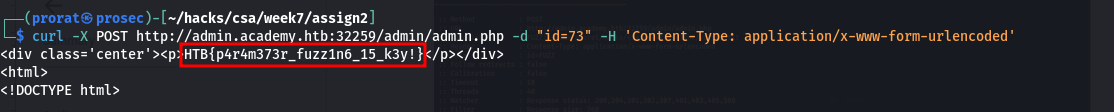
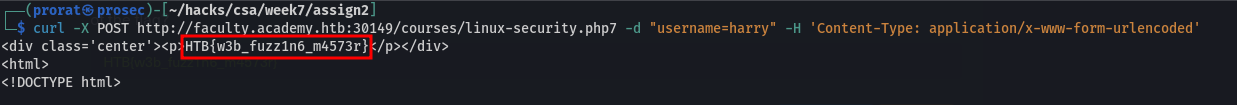
Now that we have the right parameter and its value, we use the curl command to retrieve the flag.
Skills Assessment - Web Fuzzing
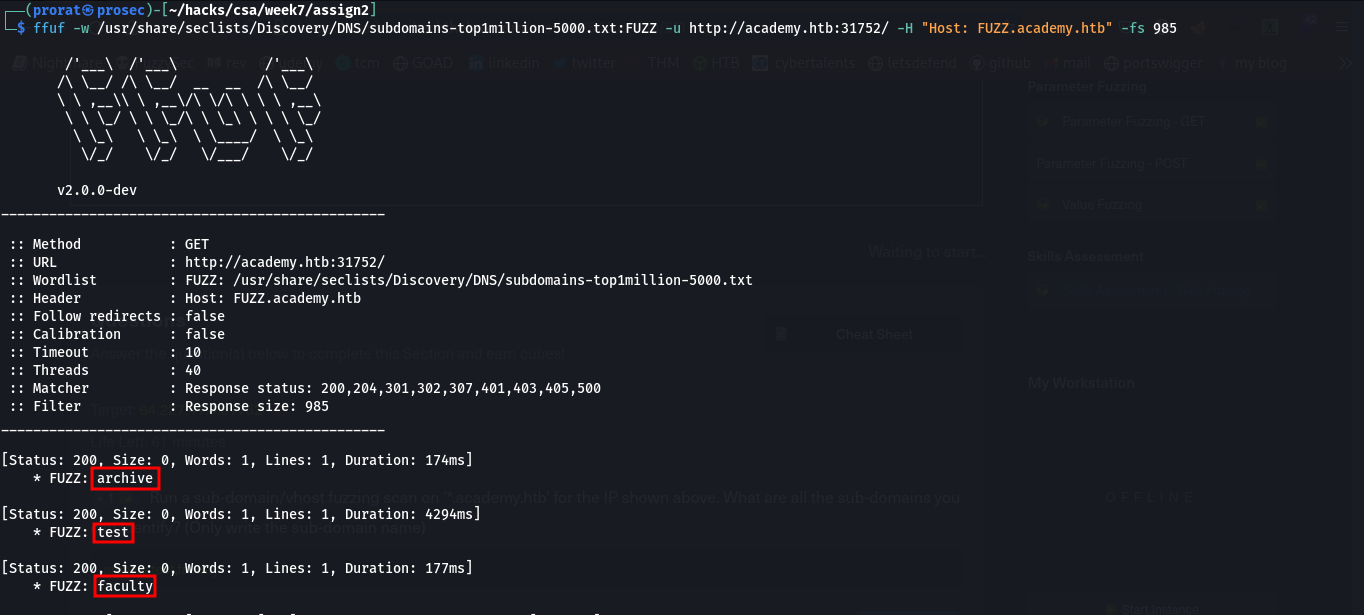
Q1. Run a sub-domain/vhost fuzzing scan on '*.academy.htb' for the IP shown above. What are all the sub-domains you can identify? (Only write the sub-domain name)
archive, test, faculty
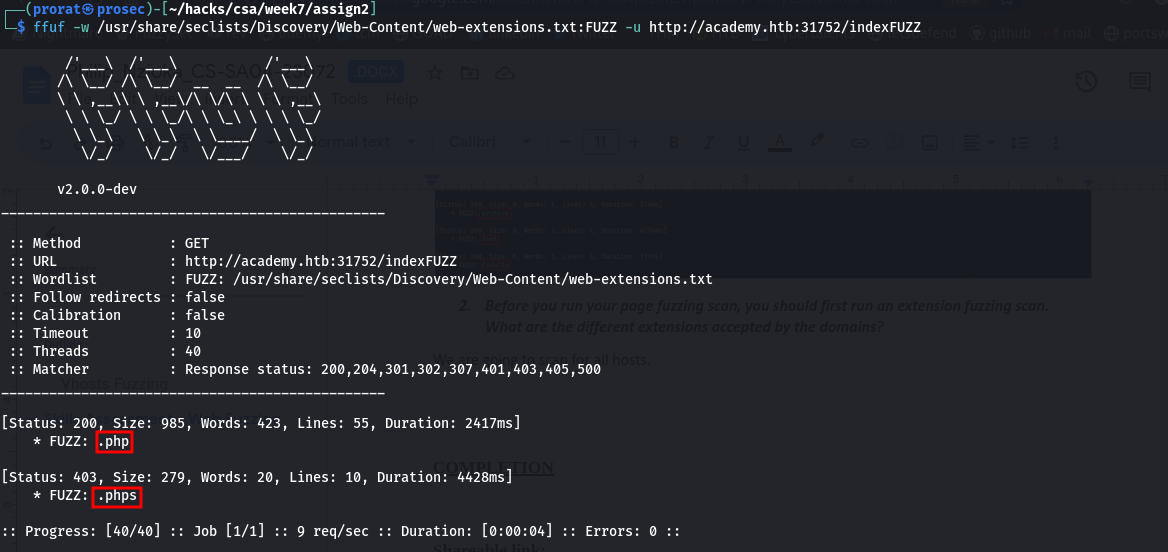
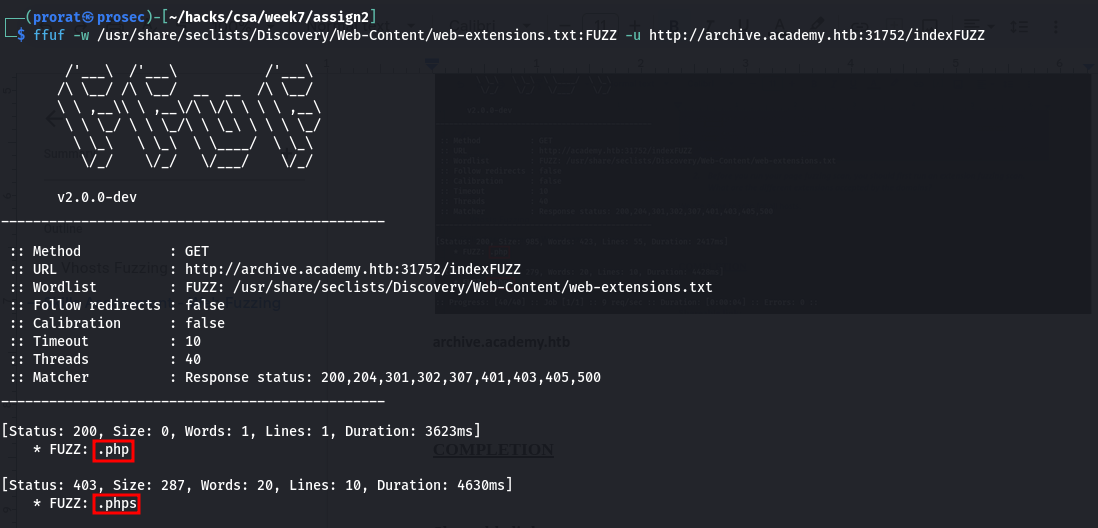
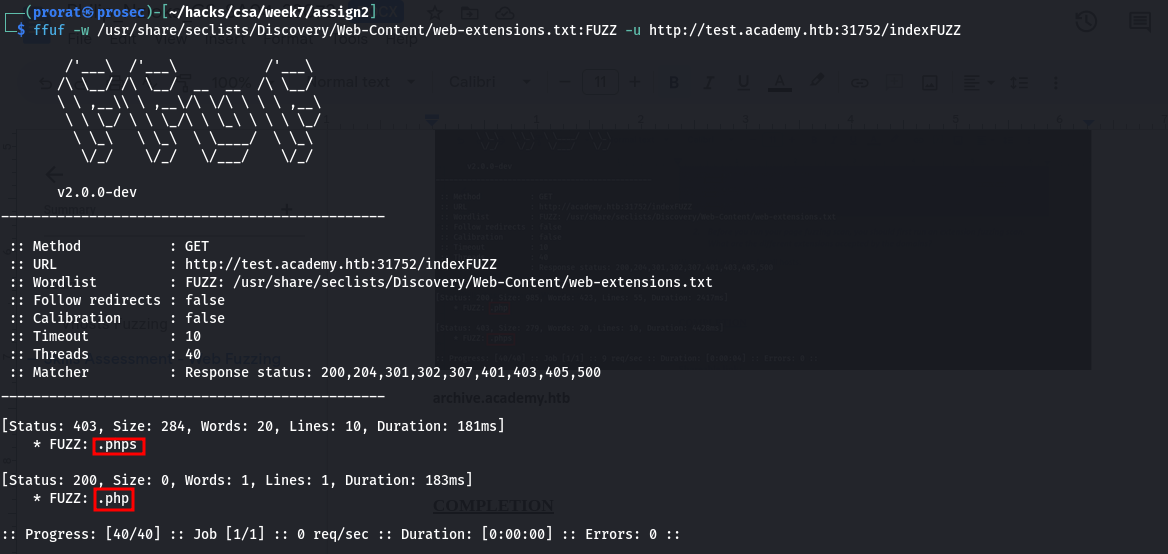
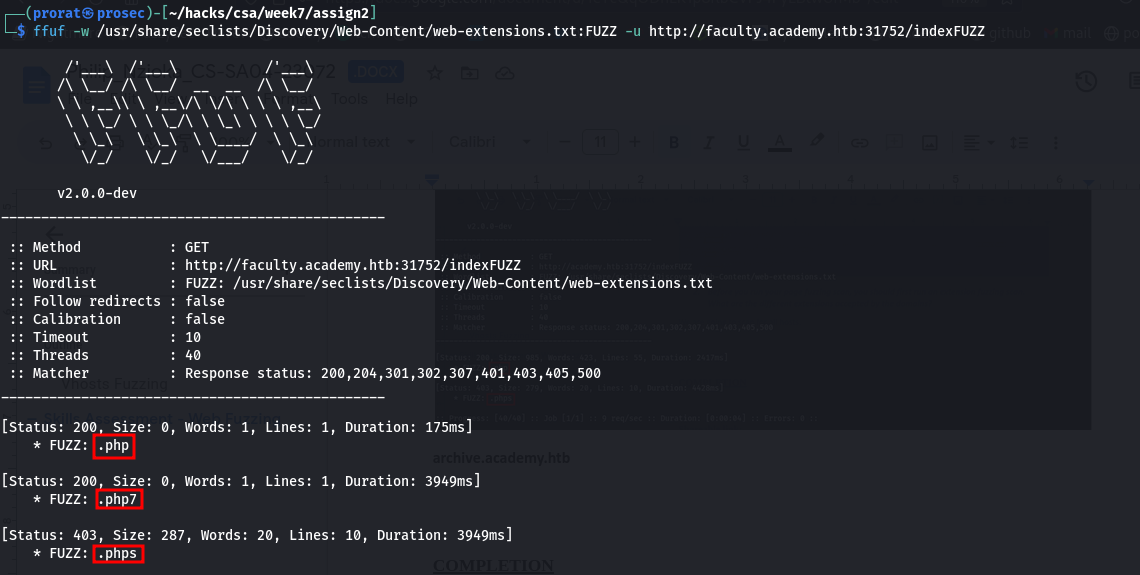
Q2. Before you run your page fuzzing scan, you should first run an extension fuzzing scan. What are the different extensions accepted by the domains?
We are going to scan for all hosts. academy.htb
archive.academy.htb
test.academy.htb
faculty.academy.htb
php, phps and php7
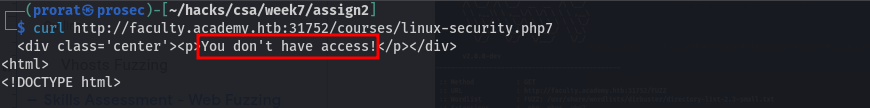
Q3. One of the pages you will identify should say 'You don't have access!'. What is the full page URL?
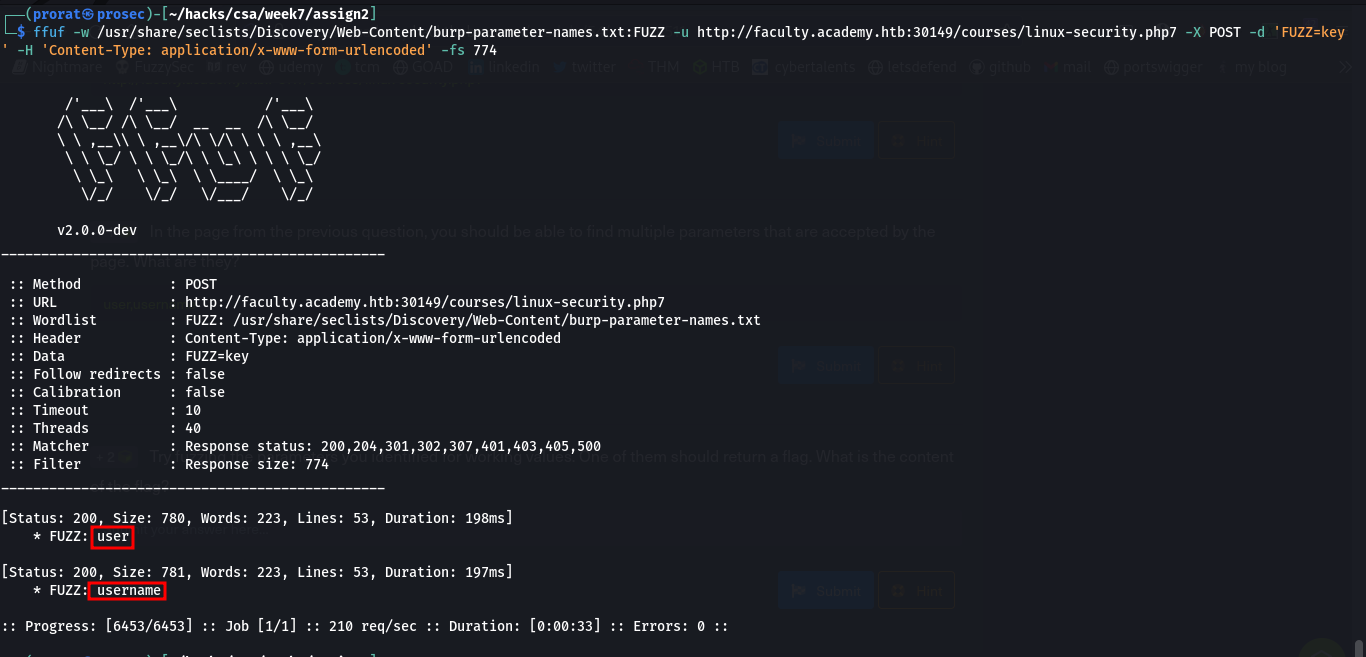
Q4. In the page from the previous question, you should be able to find multiple parameters that are accepted by the page. What are they?
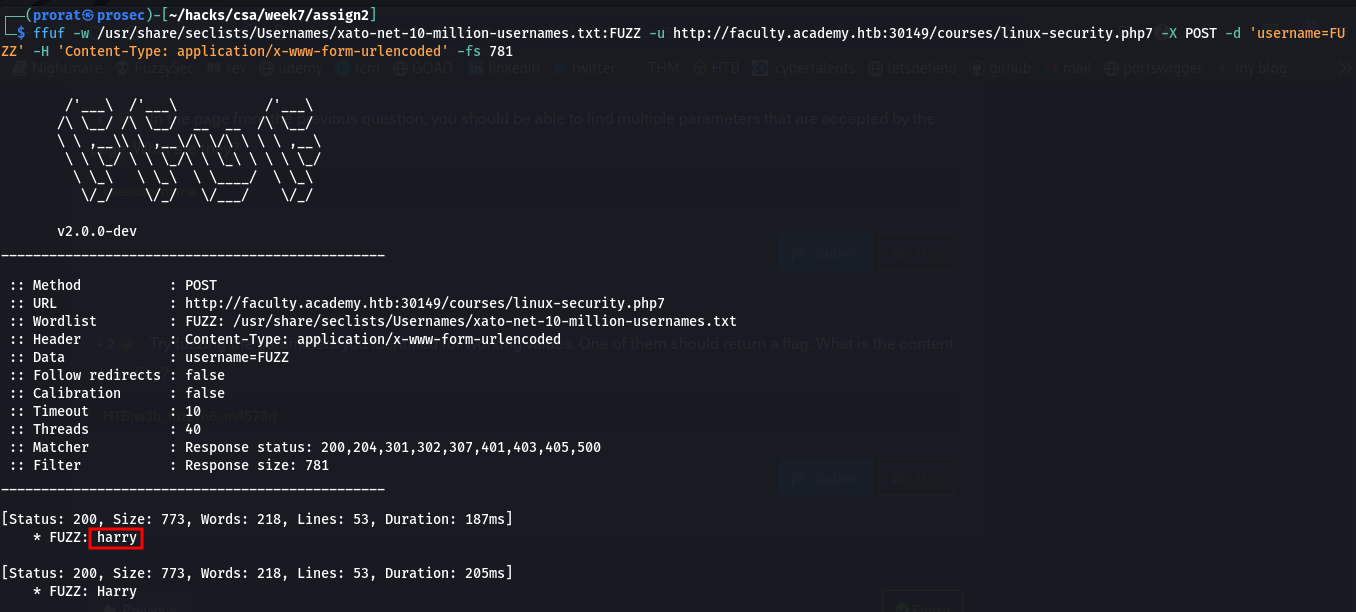
Q5. Try fuzzing the parameters you identified for working values. One of them should return a flag. What is the content of the flag?
Happy learning folks!.